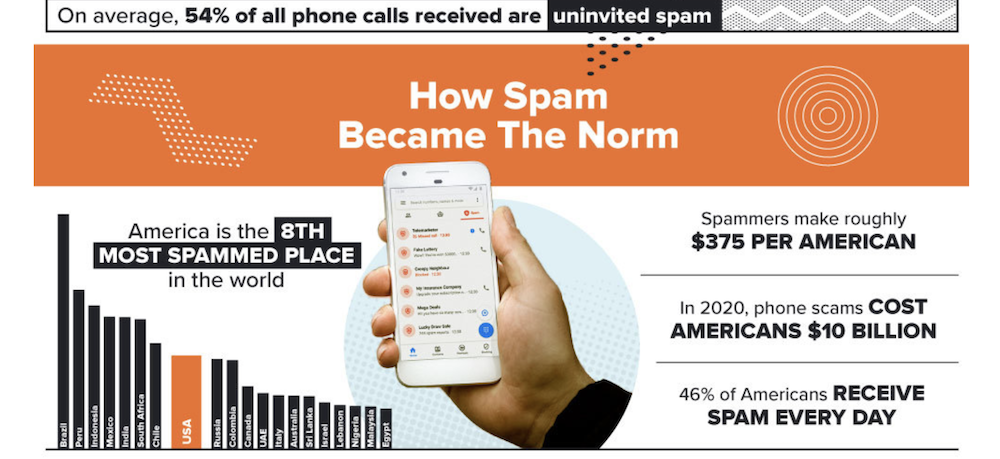
Nearly 40% of the 4-5 billion robocalls made every month are fraudulent, meaning the average US citizen receives up to 5 illegal robocalls from cybercriminals every month.
Criminals use number spoofing, the process of intentionally falsifying the phone number and name displayed on the recipient’s caller ID, to coerce unsuspecting individuals into revealing sensitive personal information like bank account data, social security numbers, passwords, and more.
Because the scammers alter their real phone numbers to make it look like these phone calls are coming from local numbers, banks, or even reputable agencies like the IRS, it’s all too easy for recipients to mistake spoofed numbers and fraudulent “representatives” for the real thing.
To combat caller ID/number spoofing, the FCC developed the STIR/SHAKEN caller identification and authentication protocols, as well as the framework needed to implement them.
Table of Contents:
- What Is STIR/SHAKEN?
- How Does STIR/SHAKEN Work?
- Why Is STIR/SHAKEN Important?
- STIR/SHAKEN: What It Can and Can’t Do
- STIR/SHAKEN FAQS
What Is STIR/SHAKEN?
STIR/SHAKEN is a series of technical protocols and implementation procedures designed to help verify the information displayed on your Caller ID when you receive an incoming call on IP networks.
Its main goal is to cut down on the number of fraudulent robocalls, thereby reducing incidents of identity theft and other VoIP security threats.
In brief, STIR/SHAKEN “signs off” on displayed caller identification information by using data stored in initiating, terminating, and external carriers within interconnected networks to verify the Caller ID as legitimate.
STIR
STIR, short for Secure Telephony Identity Revisited, is an IETF (Internet Task Engineering Force) working group responsible for outlining the technical protocols required to create a digital signature for a VoIP phone call.
These digital signatures (sometimes called digital certificates) use SIP data to provide information about the caller’s identity and the call origin, as well as information about the terminating provider.
STIR was developed by the Internet Engineering Task Force (IETF) in February of 2018 and first was published as RFC 8824 as an update to previous robocall legislation.
In short: STIR is a set of technical protocols created by the IETF to help verify/authenticate the calling party’s identification, ensuring that the person/company calling you is actually the person/company you’re speaking with. It is focused mainly on end devices.
SHAKEN
SHAKEN, short for Secure Handling of Asserted Information Using Tokens, is a framework that outlines and defines the ways in which service providers actually implement STIR technology to authenticate calls made/received over the IP network.
It was developed by the SIP Forum and the ATIS (Alliance for Telecommunications Industry Solutions) as a response to STIR.
In short: SHAKEN are standards for how service providers manage STIR-authenticated calls in their networks. It is focused mainly on the actual deployment/implementation process of STIR across carrier networks/service providers.
How Does STIR/SHAKEN Work?
In simple terms, STIR/SHAKEN works by using standard cryptography key infrastructures that allow service providers to authenticate and verify SIP phone call headers.
Of course, the process itself is much more complicated than that, and it can get pretty confusing given the technical language.
We stated above that STIR/SHAKEN relies on digital certificates/digital signatures to ensure that the person making the phone call is who they say they are.
But where do these certificates actually come from?
The below 8 steps, illustrated in the image below, outline the entire STIR/SHAKEN Authentication protocol.
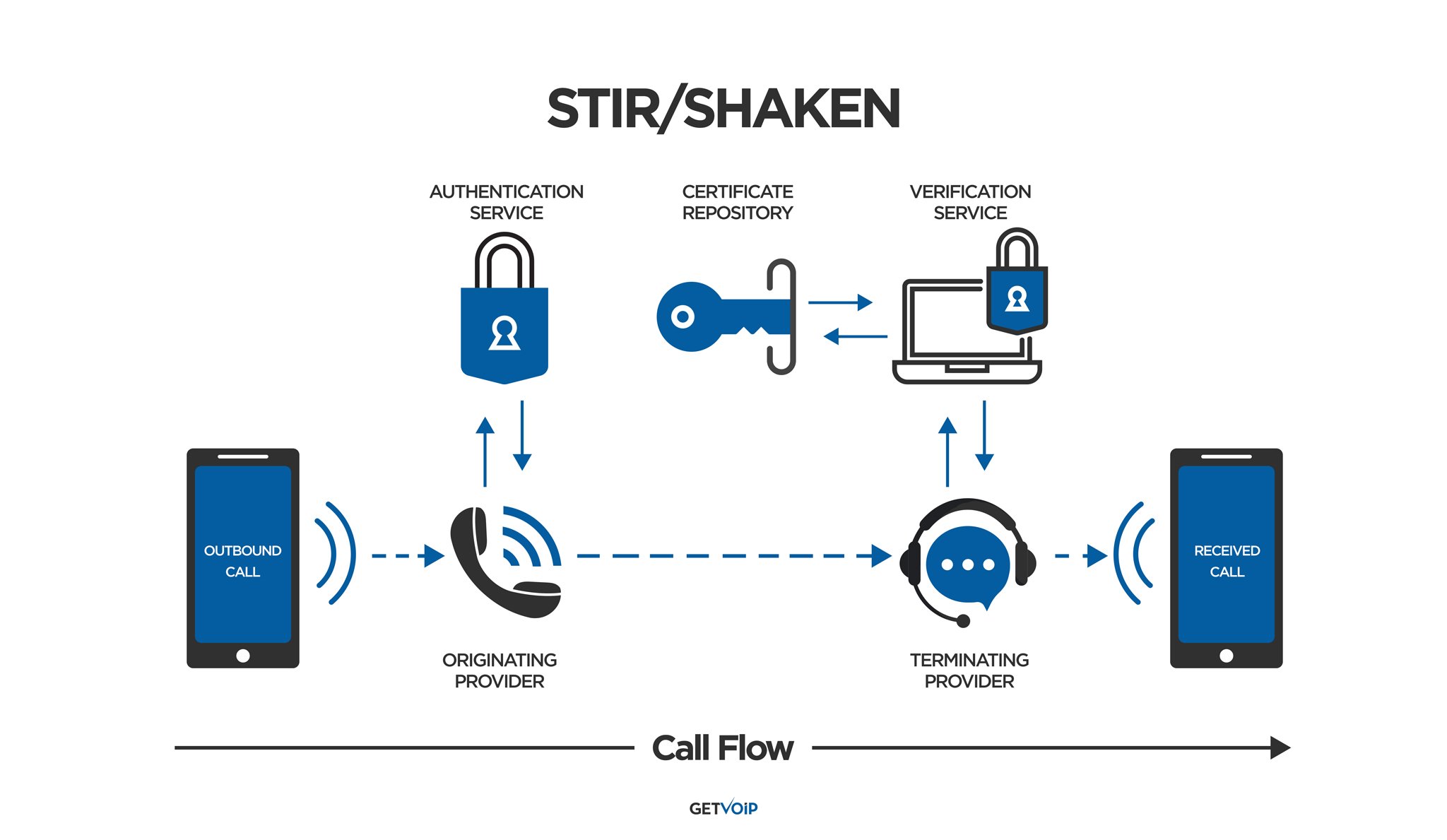
Step 1: Receiving the SIP Invite Assigning The Attestation Level
First, the VoIP provider examines the phone number the person initiating the call (we’ll call him Dave) is calling from.
The originating provider also receives a SIP Invite, which is essentially an “invitation” to assist in verifying and sending the call forward.
Before anything else happens, the initiating service provider needs to assign an Attestation Level to the call source.
Step 2: The Attestation Level is Assigned
Full Attestation (Level A) means the service provider verifies that Dave is allowed to use the number he is calling from.
Partial Attestation (Level B) means that Dave’s provider can verify the call origination point, but can’t verify if Dave is actually authorized to make calls from the number.
Gateway Attestation (Level C) means Dave’s provider verifies where the call was received from, but can’t verify the source of the call.
Once the Attestation Level is assigned, things can move forward.
Step 3: The Initial Service Provider Creates a SIP Identity Header
Dave’s VoIP provider looks at all the caller ID tags and related phone numbers that they provide Dave, verifying that Dave is actually Dave.
As proof, the provider attaches an encrypted digital certificate of authentication to the SIP Header.
The SIP Header contains key information like the caller and recipient’s phone numbers, the current timestamp, the attestation level, and the origination identifier.
Step 4: The Terminating Service Provider Receives the SIP Header
The receiving service provider decrypts that certificate, reads all the data in the SIP Header, and “learns” that the phone number does indeed belong to Dave — according to the originating service provider, that is.
Step 5: The SIP Invite and SIP Header Are Sent for Verification
To be sure, the terminating provider sends that SIP header to a Verification Service.
Step 6: The Verification Service Runs Its Own Tests
Once received, the Verification Service examines the digital certificate and runs it through additional databases, including known spam databases and certificate repositories from other service providers.
Step 7: The Verification Service Returns SIP Header to the Terminating Provider
Once the Verification Service authenticates the SIP Header via public keys and the public certificate repository, things move forward.
Step 8: The Intended Recipient Receives the Call
Once Dave’s identity is completely verified and authenticated according to STIR/SHAKEN standards, the call is sent to the intended recipient.
To summarize:
- The provider initiating the call receives a SIP Invite, which determines the level of attestation the call needs
- The provider sends that SIP Invite to an Authentication Service
- The Authentication Service sends the SIP Header, which includes digital signatures/certifications (called PASSporTs) back to the initial service provider
- The SIP Header, with relevant certificates attached, is sent to the Terminating Service Provider (the recipient of the call)
- The Termination Service Provider sends that SIP Header to an additional Verification Service
- The Verification Service sends the SIP Header to a Certificate Repository that provides another level of verification by decoding the SIP Header data
- The Verification Service sends the SIP Header back to the terminating provider with information on whether or not the Caller ID is valid
- If valid, the termination provider sends the call to the intended recipient
Why Is STIR/SHAKEN Important?
While the process of understanding how STIR/SHAKEN works and what it actually does is a bit complicated, the most important thing to remember is that this extra level of protection offers some major benefits to your business.
Let’s take a look at some of these benefits below.
Spam Protection
Think your team knows better than to answer calls from unidentified, unfamiliar, or outright spam phone numbers?
Think again.
Studies show that 65% of calls that display a business name on caller ID screens are answered – even if the business is unfamiliar. Plus, 18% of calls from unidentified numbers are answered, while nearly 9% of calls that come from numbers identified as spam are answered.
Not only that, but Americans lost nearly $30 billion to robocall scammers in 2020 — and that number is only expected to rise as businesses return to more normal operations after the pandemic.
Using a VoIP software provider that implements STIR/SHAKEN protocols significantly lowers your chances of receiving these dangerous calls. Remember, it just takes one employee to reveal passwords to the kind of sensitive data that could lead to millions of dollars in lawsuits.
Robocall Reduction
No one likes to answer the phone and hear the droning of a robocall recording.
These calls are relentless, incredibly annoying, and often get in the way of office productivity.
Every minute your team wastes on trying to determine whether or not the guy on the other end of the line offering a free around-the-world cruise is real means time that could have been spent selling, working on upcoming projects, or answering customer service calls is lost.
Spammers and robocalls waste billions of productivity hours each year, and more than half a billion dollars in lost revenue because of that wasted time.
STIR/SHAKEN helps you to get that time — and that lost revenue — back.
A Protected Reputation
Remember that STIR/SHAKEN doesn’t just help to cut down on the number of robocalls and potential scammers your business comes into contact with.
It also helps to protect your business by significantly lowering the chances that your own business telephone number will be stolen and used by these same number spoofers.
If these scammers get a hold of your company’s phone number and start using it to make annoying, unprofessional, and outright illegal robocalls? Then your company’s reputation will almost certainly be affected.
Customers will lose trust in your business, and they’ll wonder how much you care about protecting their sensitive personal information if you can’t even protect your own.
Plus, if you’re forced to change your business phone number, you’ll also lose a good portion of your contacts — especially your leads that may not yet know another way to reach you.
STIR/SHAKEN helps to keep your business in good standing by ensuring your personal or business numbers don’t fall into the wrong hands.
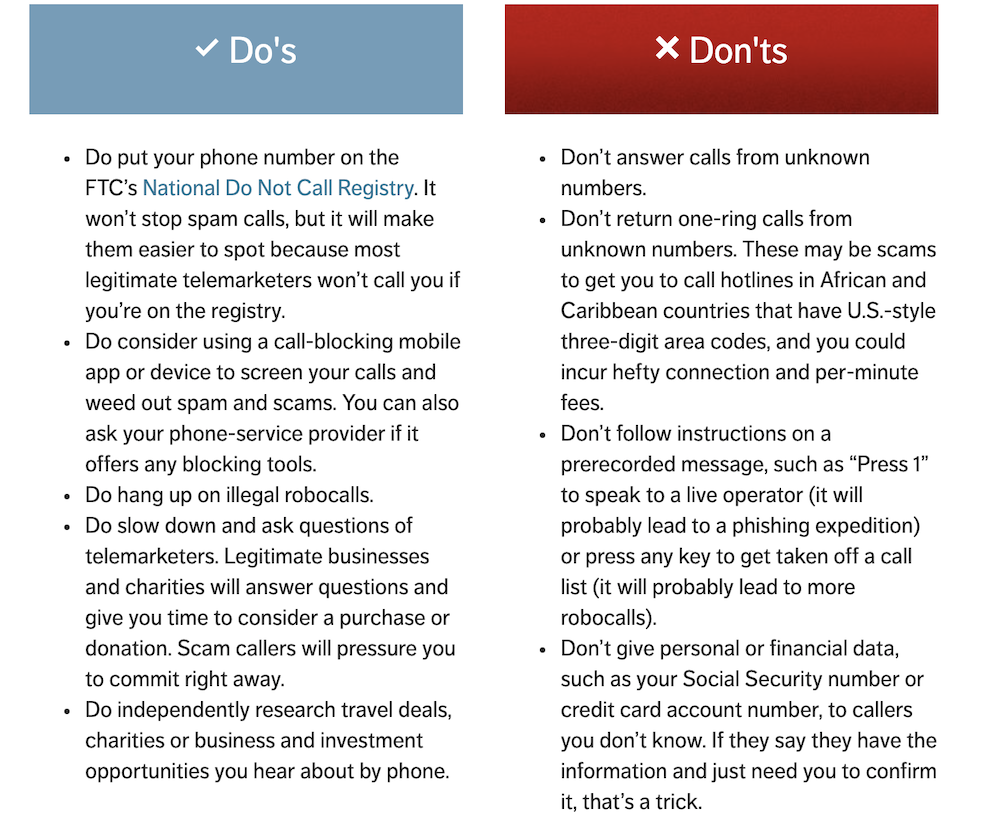
We suggest you share the below graphic with your customers, so they’ll be able to better recognize potential scams and phone number spoofing.
STIR/SHAKEN: What It Can and Can’t Do
STIR/SHAKEN is an effective way to fight robocalls and hackers, but it doesn’t guarantee that you’ll never receive a call from a spoofed number.
Note that while STIR/SHAKEN can identify previous robocall numbers, validate phone numbers, and make it much harder for spoofers to successfully steal information from you, it can’t entirely eliminate robocalls, legally punish number spoofers, or guarantee that a robocall is unwanted spam or has malicious intent.
Although STIR/SHAKEN and other security measures can’t completely eliminate the threat of hackers, VoIP providers today offer excellent network security and monitoring tools that greatly reduce the risk of cybercrimes.
Our interactive table of the top Business VoIP providers offers an overview of platforms like Nextiva, RingCentral, and Vonage, all of which have taken VoIP security to the next level.
STIR/SHAKEN FAQS
Below, we’ve answered some of the most common questions about STIR/SHAKEN.
STIR/SHAKEN refers to the set of procedures and implementation frameworks that voice service providers must put in place to prevent caller ID spoofing.
STIR/SHAKEN protocols ensure that phone calls made on VoIP phones and smartphones are coming from authenticated phone numbers. These protocols verify that the caller ID information displayed is correct, lowering the risk of spam robocalls and resulting crimes.
THE FCC required all voice service providers to implement STIR/SHAKEN in the IP portions of their networks by July 30, 2021.
These “Voice Service Providers” include:
Any service that interconnects with the PSTN network
Providers using numbers from the North American Numbering Plan (NANP)
VoIP providers
One-way VoIP providers
Faxing services
OTT Communication Providers (Over-the-Top communications providers like Google Voice, etc.)
Communication resellers
Common signs of spoofing include:
Extreme, aggressive pressure to provide personal details/account numbers over the phone
Refusal to provide a callback number
Deals that sound “too good to be true” or out of step with what the agency, business, or provider could reasonably offer
Receiving calls from unknown numbers





![What is Omnichannel Customer Service? [Benefits & Tips] What is Omnichannel Customer Service? [Benefits & Tips]](https://getvoip.com/uploads/Omni-Channel-Explained-350x203.png)