It seems as if we are at a point where data security has become an afterthought for a large number of organizations. It has become almost routine news to hear about a new data breach, and some of the names impacted would really surprise you. Just in 2018 alone, organizations including Macy’s, Adidas, Delta, Panera Bread, and even Amazon reported that customer data had been breached.
No matter the size of your business, or the industry served, security is an absolute must in the current digital climate. Unfortunately, malicious actors are out there, and are constantly developing new ways to capture and sell customer data.
This, of course, leads to massive fallout for those customers, and the organizations breached as well. A lack of trust, and potential financial consequences are not necessarily a better option than investing in properly securing your organization’s data.
When it comes to Contact Centers, or any businesses that deals with payment over the phone or Business VoIP, organizations should absolutely ensure their processes, applications, data and software are compliant with the global PCI Security Standards.
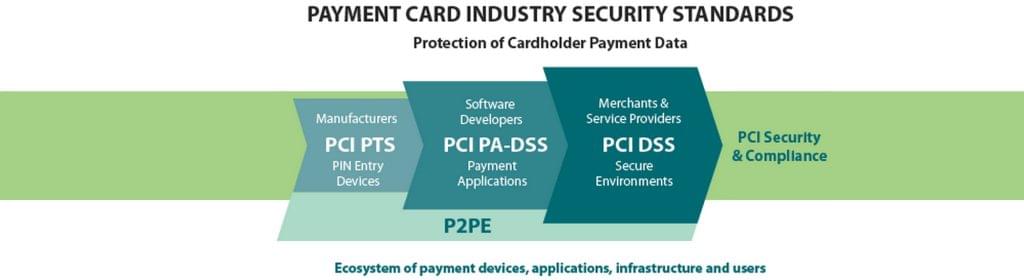
What is PCI Security Standard Compliance?
While PCI Security Standards are not set in stone through any official laws or regulations, the PCI Security Standards Council (PCI SSC) has emerged as a “global forum” to facilitate the development, enhancement and dissemination of an agreed-upon security standards for payment account security — originally founded by American Express, Discover Financial Services, JCB International, MasterCard and Visa Inc.
The PCI SSC is a global-reach, industry wide security council. The idea is that the industry can come together within this council to develop and establish a set of regulations and security standards in order to protect payment account information — things like credit card information and sensitive customer data like social security numbers.
The PCI SSC has established PCI Security Compliance standards to ensure organizations are adhered to an agreed-upon set of regulations to protect customer credit card payment information and sensitive information.
PCI Compliant businesses must meet these agreed upon security requirements, and are subject to annual assessments to ensure continually ensure compliance. At the end of the day, if your organization deals with any form of payment information, then PCI compliance is almost a necessity.
Since there is no law mandating PCI compliance, organizations that do not meet the requirements won’t face any form of legal consequences. However, if a data breach does occur, then the organization is potentially subject to financial consequences from both the PCI SSC, as well as the clients and customers impacted by the breach.
What is the Point of PCI Certification?
At the end of the day, by ensuring PCI compliance within an organization, that business is not only protecting its customer and user data, but the organization is protected from potentially drastic financial fallout and consequences as well.
The main goal of PCI compliance is to set up a global standard for organizations to agree to and abide by, in order to counter-act the large number of data breaches in recent years. According to the PCI SSC:
- “The breach or theft of cardholder data affects the entire payment card ecosystem, from the customer to the payment institution, to the organization receiving the payment.”
- When customer data is leaked, they quickly lose trust with those merchants and financial institutions
- If their information is used maliciously, customers can also face financial fallout. Credit can be negatively impacted, and it can be difficult to regain full control over the data once it has been breached
- As merchants and financial institutions lose credibility, they will eventually lose business. Customers will simply take their business elsewhere if they do not trust that their information will be safe and protected.
If your organization experiences a data breach, and did not take the proper steps to prevent attacks or establish a recovery plan, there can be some major backlash and consequences, despite a lack of legal regulations.
Organizations of course will have customers lose confidence and choose to do business elsewhere which leads to diminished sales and revenue, businesses might have to pay for the cost of reissuing new payment cards or fraud losses, and things will only become more difficult in the future.
After a data breach, organizations will then face higher subsequent cost of compliance, potential legal costs and settlements, fines and penalties and the termination of the capability to accept payment cards. At the end of the day, a data breach can ultimately lead to a business having to close their doors for good.
The Need for Security in a Digital Era
As organizations shift their communications and processes into the cloud, including data storage (specifically customer data like CRM info), security becomes an even larger concern.
Large troves of data in general are very lucrative to malicious actors seeking to profit off of this information. However, when data is archived and only utilized internally and on-site, it would be much more difficult for an attacker to access this information. However, as we have begun shifting our major data storage and business processes to the cloud, we have begun to introduce a new necessity for security.
Since data is now not being stored on site, but rather in the cloud, this data must be protected on multiple fronts. Your organization must ensure that the data is in good hands, and the provider of whatever tool you are using (Business VoIP, CRM or Cloud Contact Center platforms) ensures that data on their servers is protected and safe.
On top of data not being in your own hands, data is then transmitted through the internet, and shared on your organization’s devices. The data must be encrypted in transmission, as well as protected on those individual endpoints as well. As cloud software has enabled us to be more mobile, there are even more endpoints and devices being connected to a network and platform than ever before — and every single one of these devices is a potential weak spot for an attack.
Since data is being constantly transmitted, shared, stored, edited, archived, and moved, there have emerged many more weak points in the process where that information can be stolen — therefore in the age of cloud solutions and digital commerce, the need for security is at a new level.
PCI Compliance in Contact Centers
While any organization that deals with customer payment information should attempt to enforce PCI compliance, Call Centers and Contact Centers in particular must be careful. As their business almost entirely revolves around collecting payment account information from customers and clients, Contact Centers face a large risk of being targeted for a malicious attack.
Contact Centers are constantly dealing with clients and customers over the phone, and more recently through online chats or even SMS text messages. Every time a customer or client sends any form of payment or identifying information to an agent, that information must be secured.
Since Contact Centers in particular are also utilizing a larger number of cloud platforms that store and access this data, from CRM solutions to Call Center software to Business VoIP tools, sometimes even going further into Artificial Intelligence and Workforce Optimization, there are a lot of loose ends that need to be tied together.
Two of the primary concerns that Contact Centers should focus on include:
- Securing data from unauthorized access. Fairly straight forward. Those that are not allowed to access the data should not be able to, this would be the first step to ensuring even the most basic level of data security. This of course starts with simple security practices, like only provide passwords to administrators, routinely change passwords, utilize physical authentication methods, and secure all devices and access points.
- Customer Trust. A major aspect of any organization is that bond of trust between the client and the business. Customer’s heavily weigh their experience with an organization, and will choose to do business with those that provide the best experience. When dealing with any amount of capital or even just sensitive data (think HIPAA), customers want to know their info is protected and they will not be harmed for doing business with your organization.
These two concerns of course go hand in hand. When a customer’s data is unsecured, and breached, they will ultimately lose trust in your business. To ensure data is secure is to ensure that customer’s will continue to trust your business.
At the end of the day, preventing any form of breaches and ensuring to your clients that their data is safe can go a long way in creating that bond of trust. Contact Centers, with their vast sets of data and large number of interactions daily, must be very careful in particular, and should ensure PCI compliance at every single step of the process.
PCI Compliance in Business VoIP
When it comes to VoIP more generally, the PCI DSS “does not explicitly reference the use of VoIP.” However, this doesn’t mean that just because your organization is utilizing a Business VoIP service they are in the clear. In fact, the PCI DSS does have their own FAQ section highlighting the use of VoIP specifically.
Now, this does get a little bit tricky, but we will attempt to outline the jist of what you will need to know. PCI Compliance for VoIP gets a bit in-depth, and goes as far as defining different forms of transmissions (internal or external), as well as the sources of these transmissions.
The major takeaway is this:
To meet PCI compliance, organizations must ensure that any form of internet data, or IP network traffic, that contains any form of payment account information is secured. Simply put, payment account data transferred through “VoIP traffic that contains payment card account data is in scope for applicable PCI DSS controls.”
Since VoIP is sending the sound of your voice through the internet as data packets, that data is then subject to PCI compliance security standards as it is now information being transferred through, and stored on, your organization’s network.
But the story doesn’t really end there. Things get a bit tricky when it comes to the source of the VoIP call, and how that data is being transferred:
- Internal transmissions – VoIP traffic that contains payment card account data that is shared within your organization’s network must be PCI compliant. Any data stored, processed or transmitted internally over an organization’s network must fall in line with compliance.
- External transmissions – When an entity transfers payment card info to another business (for example, service provider or payment processor) the entity’s system and networks used for those transmissions must be compliant. Meaning, if your business places a VoIP call to send payment data to another business or entity, that connection must be secured and PCI compliant.
- External Transmissions to/from Cardholders – When VoIP is utilized for the transmissions of payment card account data between a cardholder and an organization, that business’ systems and network used for the transmission must be compliant.
This is really just the skinny of it, the PCI SSC goes really far into detail on these different scenarios. However, the easiest way to ensure your VoIP communications are PCI compliant is to treat all calls, no matter the source or destination, should be as secure as possible to meet PCI compliance.
If you want to read further, you can learn more about VoIP compliance and the very specific regulations and scenarios at the PCI SCC’s website.
How Can Your Business Adhere to PCI Compliance?
Now that we have established why your business should adhere to the compliance standards set up by the PCI SSC, we will point your organization in the right direction of starting the processes. Security is ultimately no simple task, and will require a notable amount of research and comparison to truly understand the proper direction to take.
The PCI SSC does offer a fairly basic list of requirements and associated goals to help organizations get started:
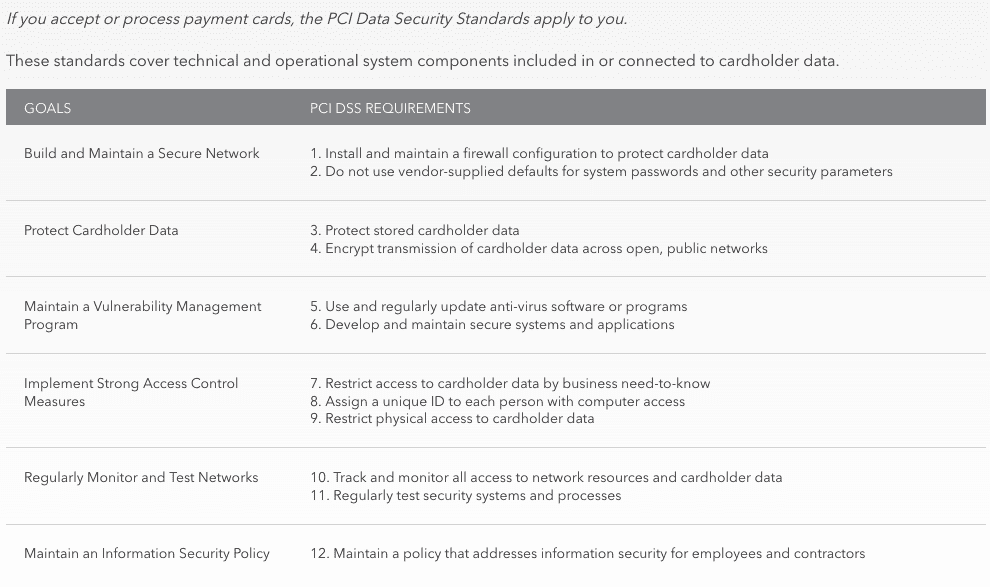
Security must be treated as an investment, spend now to save later. Spend now to protect your organization, data and customers, to avoid any potential fallout from a data breach, should it occur. Without the right security in place, it can truly happen to any business as we have seen in real-time. So far we have not seen any security complaints for inContact.
I. Ensure Solutions and Platforms are PCI Compliant
As I already mentioned, in this age of cloud platforms, most of the data we access and utilize is not even stored within our servers, or physically in the same location as which we work. With the use of CRM, Contact Center and Business VoIP platforms specifically, customer and client data are stored on the vendor’s data centers, and accessed through the internet.
Therefore, it is incredibly important that Contact Centers at a minimum ensure the tools they use, and platforms they subscribe to, ensure some level of PCI compliance. This is the same process other industries use, for example a hospital would only use a solution that is HIPAA compliant.
Just to highlight some major names:
II. Follow the PCI SSC Guide to Ensure Compliance
Unfortunately, the specific requirements for different financial institutions and payment card brands will differ on a case by case basis. Each organization will have their own specific regulations and requirements for PCI Compliance.
“Validation of compliance with the PCI Data Security Standard is determined by individual payment brands. All have agreed to incorporate the PCI Data Security Standard as part of the technical requirements for each of their data security compliance programs. The payment brands also recognize qualified security assessors and approved scanning vendors qualified by the PCI Security Standards Council.”
Because of this, the PCI SSC provides a rough outline of the three-step process that takes places to ensure compliance.
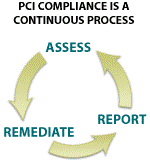
1. Assess
Assess your organization’s systems and processes related to data by identifying cardholder data, taking inventory of IT assets as well as business processes for payment card processing, and analyzing for any vulnerabilities within these systems.
This can be done through scoping, a process in which organizations identify all system components that are located within or connected to the cardholder data environment.
Scoping should be an annual process to ensure routine check-ups and maintenance, as of the best ways to prevent any potential breach is to proactively close any holes that leaks appear through.
Organizations can actually hire a qualified security assessor. According to the PCI SSC, “a Qualified Security Assessor is a data security firm that is qualified by the PCI Council to perform on-site PCI Data Security Standard assessments.” These assessors will verify technical information, use independent judgement to confirm compliance standards are met, provide support and guidance during compliance the process, and produce a final report to submit to the PCI SSC.
2. Remediate
After the assessment process, it should now be clear to your organization what must be done to close up any potential holes in the network, and prepare the system for complete PCI compliance. While this means fixing any found vulnerabilities, the PCI SSC also recommends eliminating the storage of cardholder data from your organization’s services, data centers and records unless absolutely necessary for business operation.
3. Report
Once an assessment is completed, and the organization takes the necessary steps to correct any issues and tighten up security, a report must be complied and submitted to the appropriate banks and card brands.
Again, depending on the requirements of that specific brand, organizations might have to file more frequently or follow a specific process. Some brands, for example, require organizations to file quarterly submissions.
The Bottom Line
Unfortunately, too many businesses and individuals see security as an after-thought, or a one-time process. However, the truth is that keeping our data and communications secure hasn’t ever been more important. With new risks and attacks appearing everyday, and bigger data sets becoming more and more lucrative to malicious actors, the potential for major fallout is only growing.
The PCI Data Security Standard ensures that organizations will not only enact security measures, but properly maintain and optimize them as well over time. With industry leaders working together to set a standard compliance level, organizations can help work towards a more secure digital age.
Ensuring your organization utilizes PCI compliant tools, and fulfills PCI compliance regulations where necessary, is absolutely a win-win situation for both the business and the clients. By keeping data secure, organizations can retain customer trust, and ultimately their business.


![What is Omnichannel Customer Service? [Benefits & Tips] What is Omnichannel Customer Service? [Benefits & Tips]](images/omni-channel-explained-350x203.png)