At this point, its fairly safe to say that the concept of ransomware has probably made its way into IT discussions in almost every organization. If your business hasn’t had a chance to discuss and plan for a potential attack, then the time to do so is absolutely right now.
Back in May of this year, the WannaCry ransomware attack was a massive worldwide cyberattack that held a massive number of networks hostage, forcing businesses and even hospitals to fork over ransom payments, mostly in the form of Bitcoin. This was a huge wake-up call for most organizations, and isn’t a topic that should be taken lightly in anyway. A lot of time and capital are at risk to a ransomware attack, and many businesses could crumble without the proper protection or procedure to handle an attack.
But, thankfully, just like most forms of cyberattacks, there does exist a barrier of defense; a way to protect your business and all of its assets from this tricky form of attack. So, for those unsure of how to protect themselves, we’re going to take a closer look at just exactly how a ransomware attack works, and how your business can defend itself from this nasty cybercrime.
A Brief Rundown: What Is Ransomware?
So, for those that follow our blog this won’t be something entirely new, I discussed the concept a little while back following the massive WannaCry disruption. But, it’s always useful to lay the foundation and begin with the basics, and that is understanding exactly what a ransomware attack is and why your business should be ready to defend itself.

The idea isn’t too complicated, and actually kind of self-explanatory if you take a close look at the name itself: ransomware. The basic idea is that an attacker will utilize malicious software to take control of your organization’s network, computers, or files — encrypting everything and holding it hostage. In order to break this encryption, and regain control over your company’s network, and gain the key to decrypt files, the attackers demand a ransom payment.
As we saw with the WannaCry attack, these malicious hackers will usually demand payments in some form of cryptocurrency, most commonly bitcoins. But, we’re not going to get too bogged down by the details of cryptocurrency and the blockchain technology that makes it possible. What’s more important is understanding the threat, and how to prevent the threat from reaching your shores.
How Does Ransomware Take Down an Entire Network?
Any single device that is hooked up to your network can be an access point for attackers to inject their malicious software, and take control of your network. As we saw recently, VoIP connections and IP desk phones can even serve as an attack point, but of course so can your team’s mobile devices like smart phones and tablets.
So, the scary part is that attackers don’t necessarily need to find a way into the network through computers. As soon as that malicious software finds one tiny crack, one little entrance point, it can jump from device to device to bring everything under its control.
Keep Your Network and Business Protected
Now, you can take a look at my previous ransomware post to get an idea on how to educate your team and stay secure. To sum that up briefly, I made a few key points that any business should take into account:
Always keep your apps, tools, network, firewalls (both hardware and software), session border controllers and computers updated. Even smartphone updates are routinely patching “backdoors” and exploits on these devices.
- Back up all of your data. If your network is brought down by ransomware, the threat can be avoided if your business had backups of all the crucial information, located on a completely separate network.
- Establish an incident response plan: educate and train staff to recognize potential threats, but also create a process for how to prevent the spread of any malicious software. This would mean disconnecting all devices and cutting off access to the network until the threat can be dealt with.
- Implement and maintain security software such as firewalls, but also more importantly, it might be time to consider very specialized defenses, Ransomware Protection software, which is the main focus I want to touch on with this post.
Firewalls and session border controllers are great, they act as the gate keepers to your network, preventing unwanted connections and attackers from making their way in. However, these tools can still be bypassed, and the concept of social engineering can be used to trick workers and IT staff into letting in a threat without even realizing it. Thankfully, there also exists an entire class of data protection and cybersecurity software that focuses directly on ransomware.
Utilize the Right Tools: Ransomware Protection
Some of the best defenses are what I listed above, recognizing what could be a potential threat, and stopping it right in its tracks. However, humans are not perfect, and nor are the systems they design. So, while some basic education can go a long way, and firewalls can help filter out some traffic, your team will need the right tools to detect and eliminate ransomware when it does make its way through your first lines of defense.
Here’s our rundown on some of the best Anti-ransomware tools out on the market today:
1. AVG’s Ransomware Decryption Tools
To cover all of the different ransomware threats that exist today, instead of a “one-size-fits-all” tool, AVG has released multiple tools designed to defeat specific threats, and the most common of ransomware software that is utilized. This list includes popular tools such as Apocalypse, BadBlock, Bart, Crypt888, Legion, SZFLocker, and TeslaCrypt.
If you’re unsure of what form of ransomware is impacting your network, this handy page hosted by AVG can help you identify exactly what’s going on, and how to implement the right fix for each specific threat. Protection can of course also be supplemented through AVG’s Internet Security Business Edition software.
2. Avast Free Ransomware Decryption Tools
Avast solutions are already some of the best anti-virus and anti-malware tools available on the market today, even if your business is looking to utilize a completely free solution. Just like how AVG does it, Avast has a long list of anti-ransomware tools that target and destroy specific ransomware protection.
This list extends to include 21 different strains of ransomware, and might be one of the best go-to options out there right now. Simply utilizing Avast’s anti-virus suite alone can help prevent, detect, and remove and malicious software before it spreads too far. The software also provides step-by-step instructions and guidance on how to utilize the tools to protect your business, and defeat any attacks as they occur.
3. Malwarebytes Anti-Ransomware Beta
If you are looking for a tool to almost “set it and forget it,” the Malwarebytes Anti-Ransomware Beta might be the right solution to take a close look at. Malwarebytes should be a name familiar to anyone that’s delved into antivirus software before, as the tool is know as one of the strongest malware removal platforms available. Working with a company called EasySync solutions, this MalwareBytes Anti-Ransomware tool was designed to monitor, detect, and eliminate any potential ransomware threats that make their way onto your network. The nice thing is that instead of downloading and utilizing individual tools, this one solution should have you covered for all the major threats.

According to Malwarebytes themselves, this tool “uses advanced proactive technology that monitors what ransomware is doing and stops it cold before it even touches your files. It has no shot at encrypting. And it does not rely on signatures or heuristics, so it’s light and completely compatible with antivirus.”
4. Bitdefender Anti-Ransomware Tool
While still a free tool, Bitdefender’s Anti-Ransomware Tool covers a bit of a smaller list compared to the other options. Limited to CTB-Locker, Locky, Pertya and TeslaCrypt, this tool is still capable of protecting your business from some of the biggest threats that exist. However, stand alone it might not be the strongest choice. Combine your protection with Bitdefender’s Anti-Virus suite and your business will be able to build a much stronger defense with not only ransomware protection, but overall virus and malware threats.
However, what’s really unique about Bitdefender’s approach is how it prevents ransomware from making it onto your network. These attacks don’t like to infect a device that’s already infected, as that would be in-efficient. So Bitdefender actually tricks these tools into thinking your device is already infected, as opposed to directly blocking it outright — your computer is essentially vaccinated.
5. Trend Micro Ransomware File Decryptor
So let’s say your computer is already infected, and your files are encrypted and held hostage. Just like with AVG and Avast’s approach, Trend Micro has released a File Decryptor tool to help users regain access to their files and networks. And this seems to be the grand-daddy of all other options, with the ability to decrypt files from up to 27 known forms of ransomware.
This extensive list includes the infamous WannaCry ransomware software as well, so you can rest easy knowing that you’ll have access to the right tools in case something like that massive breach ever occurs again. The only downside to these tools are that they aren’t real-time protection, but instead are tools used after an attack occurs and your files are being held hostage. But, if that’s the case, its never worth paying the ransom and you’re much better off utilizing a tool like this to potentially regain access.
6. Kaspersky Anti-Ransomware Tool
Another very well known name when it comes to anti-virus and malware protection, Kaspersky also offers their own version of ransomware protection. The Kaspersky anti-ransomware Tool was actually designed with SMB’s in mind, and is offered for download completely free. You won’t need to have any other Kaspersky tools installed to use the ransomware protection, although their name suite of protection does also offer some more advanced ransomware defenses.
This tool leverages two unique technologies from Kaspersky, called the Kaspersky Security network and System Watcher in order to identify ransomware behavior patterns in order to protect Windows-based devices and endpoints. The Kaspersky Security Network gathers information from millions of voluntary users to keep the protection tool up to date on the latest threats, and the System Watcher is “an advanced proactive security technology that scans all important system events,” to ensure no malicious attacks make it through.
7. McAfee Ransomware Interceptor
As you may have noticed, a big theme of our list is to rely on well known providers of existing cybersecurity software. This theme only continues with our next choice, McAfee’s Ransomware Interceptor. McAfee is already a well known protector of many devices around the world, and for good reason. Their Ransomware Interceptor only continues to expand their line of protection, and is actually also available as a free download to anyone and any business.

McAfee’s approach is to block ransomware in real-time, by detecting the potential threat as early as possible, and preventing file encryption before it even happens. According to McAfee themselves, their anti-ransomware tool leverages both heuristics as well as machine learning to identify any ransomware attacks as soon as possible. Back in May of 2017, McAfee also upgraded their Ransomware Interceptor to detect and prevent WannaCry ransomware malware infections, only a few short days after the major attack. This just goes to show how quickly the solution is updated and patched for new threats.
8. HitmanPro.Alert with Cryptoguard
While the name might not be too familiar to many, despite being a Sophos product, HitmanPro.Alert is still a solid choice when it comes to ransomware protection. Going beyond “old-school antivirus,” this tool proactively seeks out and analyzes suspicious behaviors and activities in real time to provide the best protection possible, even for entirely new threats. This means that HitmanPro.Alert is not only looking for specific ransomware software, but rather looking for “ransomware-style behavior.”
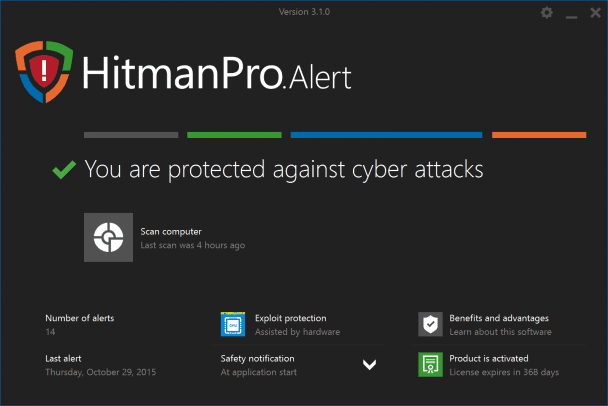
The idea is that by searching for the behavior of these malicious attacks, HitmanPro.Alert is able to stop entirely new threats without first having to identify them. For example, of a file on your machine becomes encrypted, HitmanPro.Alert will make a backup of that file, and if more files are encrypted, then HitmanPro.Alert will recognize this as a ransomware attack. The tool then “rolls back the encryption” by replacing the encrypted files with the saved backups, essentially rendering the ransomware completely useless.
9. Sophos Intercept X
As the parent company that recently acquired the team behind HitmanPro.Alert, Sophos has their own massive portfolio of cybersecurity software, including popular enterprise solutions. In fact, Sophos Intercept X was included in a recent Gartner Magic Quadrant for Endpoint Protection Platforms. Intercept X also works similar to that of HitmanPro.Alert, by proactively blocking ransomware attacks as they happen.

According to Sophos, Intercept X “utilizes the unique CryptoGuard technology” and it “works by detecting and stopping ransomware from encrypting your files, including the recent Wanna ransomware outbreak.” Intercept X compliments and works along side existing security apps, and helps to block any unwanted processes that attempt to make unauthorized modifications to your data. Now, Intercept X is more than just a ransomware protection tool, and enables even more protection for your business, like threat analysis to provide insight into potential attacks.
10. Check Point ZoneAlarm Anti-Ransomware
Based on Check Point’s larger, more robust, Enterprise security software, ZoneAlarm Anti-Ransomware brings its source code from a proven testing ground. This means you can at least put piece of mind in the name, just like with our other popular choices. Also similar to other choices on our list, ZoneAlarm attempts to find ransomware through behavior analysis, always scanning to see if and when your files are being encrypted by a ransomware attack.
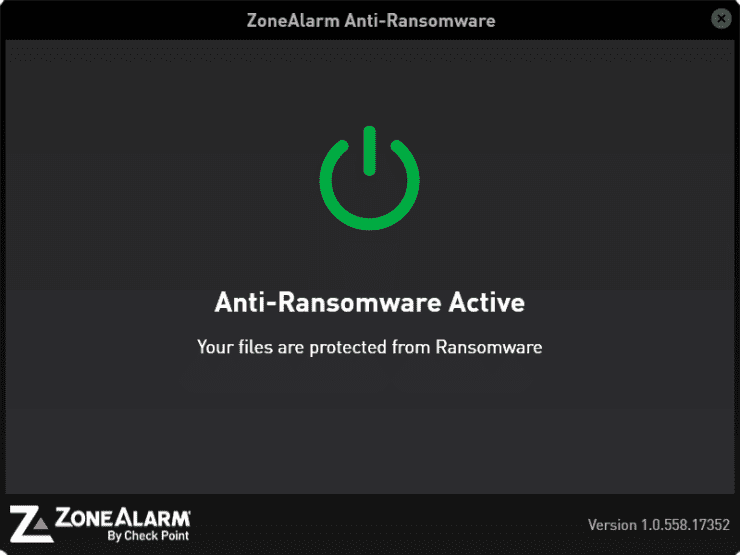
The entire application is incredibly lightweight and simple to use as well. The main screen simply shows that you are being protected, and when an attack occurs, the defenses swoop in to save the day without requiring any tooling around from end users. Once an attack is stopped, users then gain the ability to unlock their files and completely remove the unwanted malware from their machine. While the solution isn’t free, the small cost is definitely worth the piece of mind, and ease of use.