Ransomware attacks have been at the forefront of cybersecurity discussions for some time now — and for good reason. The WannaCry incident perfectly exampled how massively widespread the issue of cyber security can expand. One seemingly innocent email was enough to almost bring very crucial systems and networks down, effectively shutting off major industries around the globe. But is the threat of ransomware the only attack we should be focusing on?
It’s a good idea to agree that general cybersecurity should be a critical priority for any business, but without a strong understanding of where the threats lie, it can be difficult to utilize the proper defense. Ransomware is a real threat, but if all our efforts are focused on the idea of an invasion by land, what happens when the invasion is by sea or air?
Since Cisco just released their 2017 Midyear Cybersecurity report, we wanted to take a look at the biggest threats currently facing businesses — from the SMB, all the way up to the giant enterprise.
A Shift In The Landscape
While Cisco’s report focused on a large number of major findings, one overall conclusion to understand is that the landscape of cyberattacks is very complex, and the landscape is always moving. Or, more importantly, the landscape of cyberattacks will always be moving — these are constantly shifting goal posts. As new attack strategies are uncovered, new defense strategies pop up to block off the previously “unlocked doors,” so to say. And as new defenses pop up, new or even old attack strategies are developed or redeveloped. And these attacks pose a real threat to any business, with potential capital loss.
Weak security practices and the inflexible nature of enterprise-level organizations can leave massive gaps in the overall network defense. However, that does not mean that IT departments should be rebuilding their entire structure every single year.
Rather, utilize information and reports to keep a close eye on the trends that propose the biggest threat at any given time. At the same time, we cannot forget our foundation and the basis of which we build our defenses around, because history truly does repeat itself. VoIP attacks are rising, and attackers can even figure out what you’re typing just from listening in on a Skype call.
Cisco’s Major Findings in 2017
Now that we laid the foundation for a constantly shifting landscape, we can take a look at Cisco’s findings, and just exactly how the landscape for attacks has begun to shift.
- The dramatic increase in cyber attack frequency, complexity, and size over the past year suggest that “the economics of hacking have turned a new corner.” The modern hacking community is benefiting from quick and easy access to a range of useful and low-cost resources.
- While the cloud is a major focus, it is routinely being ignored when it comes to security. Open authorization risk and poor management of single privileged user accounts can create security gaps that adversaries can easily exploit. According to Cisco’s report, hackers have already moved to the cloud, and are working to breach corporate cloud environments.
- Business email compromise (BEC) is now a “highly lucrative” threat vector for attackers. The Internet Crime Complaint Center reported that $5.3 billion USD was stolen due to BEC between October 2013 and December 2016. For the sake of comparison, ransomware stole $1 billion in 2016.
- The Internet of Things absolutely needs to be secured, and is already being exploited by attackers. Defenders simply are not aware of what IoT devices are connected to on their network, and therefore are not aware of what is at risk.
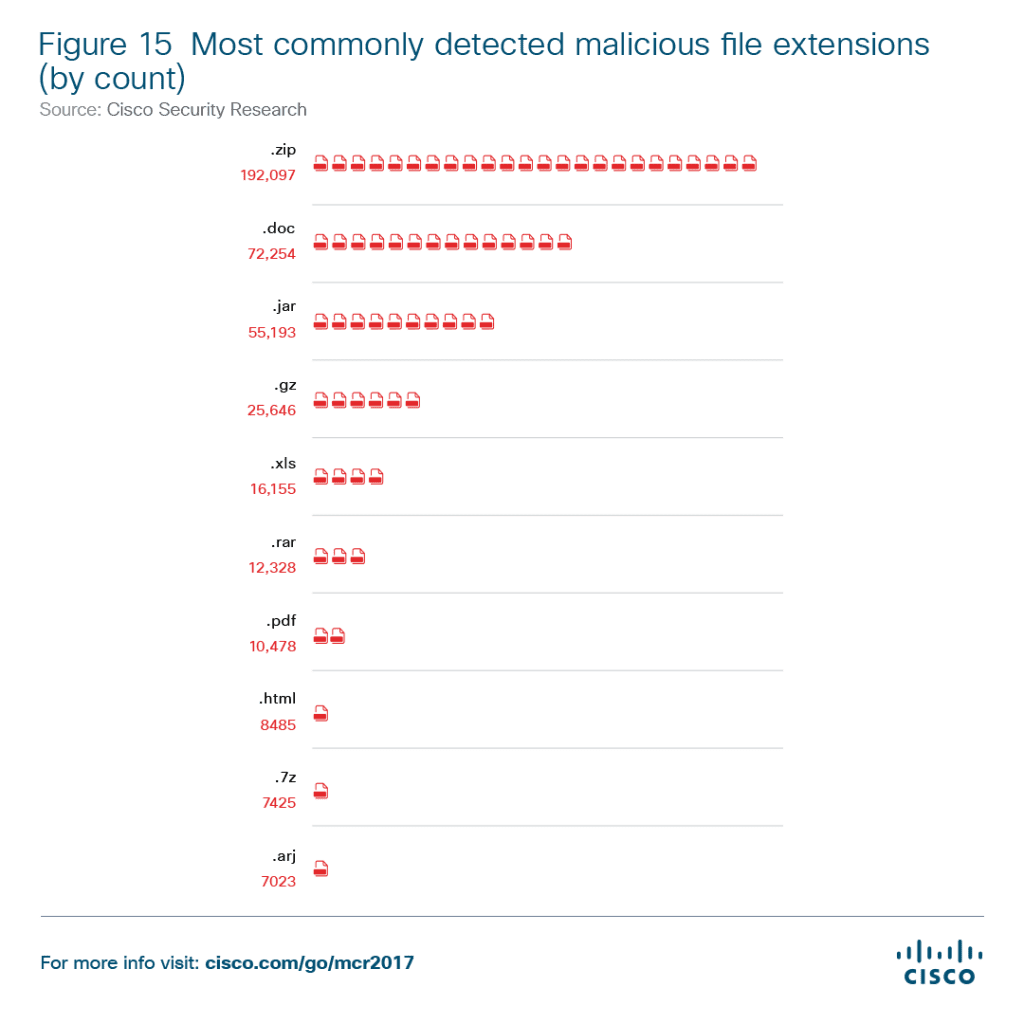
- Cisco observed an overall increase in spam volume since mid-2016, which “seems to coincide with a significant decline in exploit kit activity during the same period.” This means that attackers utilizing “exploit kit” tools have had to revert back to the old method of spam emails, as exploit kit defense has only increased. These spam emails simply contain attachments, like word documents, that are “macro-laden malicious documents.”
- Spyware that masks itself as a Potentially Unwanted Application (PUA) is, in fact, a form of malware. This software proposes a risk to security and information, but is generally dismissed or at least underestimated. Shadow IT can easily lead to a rise in PUA usage.
This shifting landscape can be seen throughout these major findings — new methods of attack are popular and are doing major damage, including BEC fraud. At the same time, the growth of the cloud and other new technologies like IoT are opening entirely new avenues of attack. And while new technologies open new fronts of battle, attackers are still utilizing old-school methods of attack and organizations are routinely forgetting about these points of access — especially email.
Security practices have improved over time, as Cisco pointed out. For example, automatic security updates are pretty much the standard in modern operating systems, even on our smartphones. We all may find it annoying that Microsoft forces us to update to Windows 10, or that Apple won’t stop bugging us to update to the latest iOS version, but these updates are simply for our protection.
But with updates being pushed out at a rapid pace, cyber criminals are simply shifting their focus back to email and malware specifically. These can almost be seen as “legacy” threats that have always existed, but are just being used in new ways.
Old Meets New
What’s really interesting to see is the intersect of old and new: old methodologies are being combined with new forms of attack. Modern ransomware attacks are being carried out by using the age-old method of placing malicious files into an email, and hoping someone will just download and open the file without giving it second thought. As the report explained:
“Cyber criminals, likely in response to the shifts in the exploit kit marketplace, have been turning to (or back to) email to deliver ransomware and other malware quickly and cost-effectively. They are also getting creative with their methods to evade detection. For example, Cisco threat researchers have observed growth in spam containing macro-laden malicious documents, including Word documents, Excel files, and PDFs, that can defeat many sandboxing technologies by requiring user interaction to infect systems and deliver payloads.”
Cisco noted that this rise in spam and malicious email coincides with a decline, or stagnation, in what are called “exploit kit” attacks. Exploit kits are essentially tools that allow hackers to gain access through a known exploit. The popular Flash plug-in for websites is known for its security holes, and if you have been paying attention to the internet, you’ll notice Flash is being phased out by all major web browsers for this main reason.
As updates continue to be pushed and Flash usage declines, so has the usage of the “exploit kits” that allow hackers to gain access through Flash. This has lead the hackers to go back to email, and email specifically as it allows direct access to the user’s endpoint.
Through some basic “social engineering,” attackers can have unsuspecting victims open up a Word Document, thinking it’s from their best friend, and the next thing they know their entire network is under attack. These attacks can come in all different, familiar files.
But the report warns that email is not only susceptible to malicious phishing scams. In fact, BEC fraud might even be a bigger concern than ransomware.
Understanding BEC
Of course ransomware is getting all the limelight right now, but the report hopes to point out an even bigger threat that is costing even the largest businesses like Google and Facebook millions of dollars.
I’ll let Cisco explain this one:
“A BEC campaign involves an email delivered to financial employees who can send funds by wire transfer. The adversaries have usually done some research on the company hierarchy and its employees– for example, using social network profiles to piece together a likely chain of command. The email may appear to be from the CEO or another top executive, asking the recipient to send a wire payment to a supposed business associate or to pay a vendor.”
Of course, a lot of effort and planning goes into this, and the attacker will generally express urgency to trick victims into acting without double checking. Cisco notes that these attacks focus on big targets — like Google and Facebook — and these targets have actually fallen for them despite operating and maintaining mature threat defenses as well as safeguards against this type of fraud.
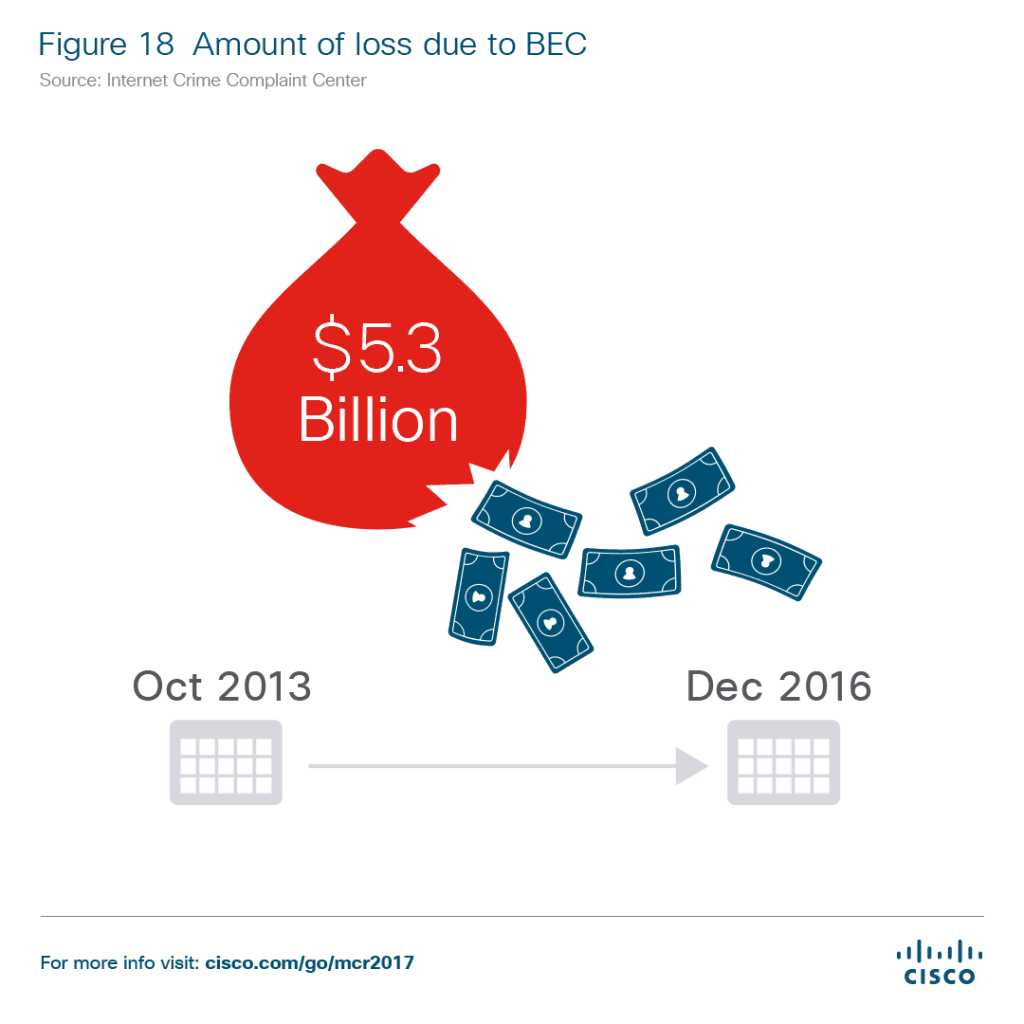
Cisco also notes that since these emails generally rely on social engineering, they do not contain any malware or file attachments and can therefore bypass standard threat monitoring tools. As we noted above, the threat of BEC is so massive that the Internet Crime Compliant Center has reported that $5.3 billion was stolen because of it between Oct 2013 and Dec 2016. That’s an average of $1.7 billion per year.
New Technologies Open Up New Threats
Email itself is now a grandfather compared to recent technology developments, including a strong focus on collaboration tools and Unified Communications. And if email is anything to go off of, chances are that our new technology will remain sustainable to attack down the line in the future as well, unless we make a major change.
The Internet of Things is already emerging, but with a known flaw: security is a second thought. Most of these tools simply leave the front door unlocked, and despite the IoT only beginning to show its head, Cisco reports that “the IoT botnets are already here.” In fact, the report notes that in 2016, “cyber attacks were launched from multiple connected devices turned into botnets.”
These DDoS attacks utilized an army of connected devices (as opposed to infected computers) to overflow and shutdown the networks of security blogger Brian Krebs, French hosting company OVH, and internet performance management company DynDNS. In fact, in their report, Cisco highlighted three known IoT botnets — Mirai, BrickerBot and Hajime — with an in-depth analysis of each.
While the IoT is only beginning to show its potential to the enterprise, the network is already being utilized for cyber attacks — a clear indication of how crucial security must be for any solution.
UC Can Help Your Business Stay Safe
Probably the most important question to ask is just how your business can stay safe with constantly changing threats. It seems as if new attack methods pop up the second one is secured. Despite all of our advancements in email, encryption, and overall security, we still have to be weary of that document that Jim from Accounting sent you. At the end of the day, even the largest defense can call victim to a little social engineering.
It might be a little a short sighted to claim Unified Communications can swoop in and save the day, but I think the benefits brought by a UC platform can help alleviate the inflexibility that might have left some teams otherwise incapable of responding to a threat. This is not to say UC is the only defense your team needs, in fact every business should be working with security experts to ensure the highest level of security available. Between firewalls and session border controllers, there exists a long list of the necessary tools widely available that do not require a massive capital investment.
On the other hand, Cisco also noted that SMBs are more susceptible to attacks than large enterprise organizations for a few reasons, but highlighted that large organizations are most likely to have “written formal strategies in place.” SMBs can improve their defense by simply improving both policies and procedures.
- Utilizing UC platforms can remove the need for email, and email attachments. This could be extended to file sharing services all around, for example Google Drive or Dropbox. But, with the ability to directly send files over the encrypted platform, or integrations for these file sharing services, replacing email with UC just makes the most sense. The ability to drag and drop files into a secure platform, as well as the capability to instantly message anyone on the team, means users can stay in touch instantly. Instead of opening that file, maybe send the recipient a quick message to verify its legitimacy.
- Defeat Shadow IT once and for all – this can be done both by finding the proper UC platform that works for your team, one that hits all the right points and is easy to use. If your team is happy with the solution, they won’t have the need to bring in their own tools, leading to shadow IT. Blocking websites and tools leads to teams working around blocks, but establishing accepted use policies can help prevent the spread of Shadow IT, and hopefully the spread of PUAs and malware.
- Spread awareness and train teams to be alert for potential threats. Don’t just block all your employees from visiting websites or sharing files, but rather establish policies for identifying potential threats. If teams are aware of unique email fraud attempts, they can prevent this form of social engineering instead of falling victim. Cisco specifically recommends requiring employees to simply place a phone call to verify the legitimacy of a request, but we think this is where UC really shines with both instant messaging and presence indication.
- Embrace a shared responsibility for cloud security: Cisco noted that 60% of users never log out of active sessions in cloud tools. This may not seem like such a big deal, but an open endpoint like that is just like leaving your front door wide open. Applying the same “best practices” that a business might in on-0remesis environments can be an effective way to help prevent unauthorized access to a platform.