You’d have to be living under a rock to not be aware of the WannaCry ransomware attack that happened earlier this year. But, on the flip side, you’d also have to be living under a rock for WannaCry to be at the forefront of your mind, still.
We live in a world where information is constantly flowing, with new developments around the globe being heard in a matter of minutes. So, it would be completely normal for most to have forgotten about this massive attack. Yet it would also be unwise to forget all about WannaCry and the concept of ransomware because this certainly wasn’t the first attack, nor will not be the last.
With cybercriminals able to target one of widest used Operating Systems and bring down 230,000 computers and related businesses to their knees, ransomware is a very real threat, and one that should not be forgotten.
What Is Ransomware?
Well, chances are that most are aware of what Ransomware is at this point. But if you’re not, it’s a great time to learn. The concept itself is fairly basic and almost self-explanatory with the word “ransom” right in the name. Basically, ransomware is like holding the files and information on your computer hostage, then demanding a ransom to release the hostage. But, just to be even more clear, let’s get a technical definition out of the way.
Ransomware is a “family of computer bugs,” or malicious attack software, that essentially locks up an infected device by encrypting all files and requiring a specific “encryption key” to unlock it. Now this doesn’t just affect your old desktop computer, but it could even impact your mobile phone, tablet or server.
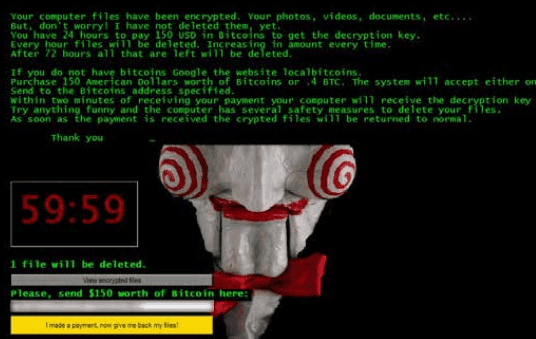
Once the endpoint device is encrypted, the owner or user of the device cannot access any files or functions on that device. To regain access to this device, the user must then pay a “ransom,” some fee amount, to receive access to their files and device again.
So without a doubt, the easiest way to understand the concept is that someone is keeping your files or entire device hostage. If you don’t pay up, you’ll never see those pictures of your child again — or, more importantly, those incredibly sensitive business related documents.
How Big is The Threat?
Just a few months prior to the massive WannaCry attack, IBM Security released a report that took a close look at the state and future of ransomware attacks. In the report, “Ransomware: How consumers and businesses value their data”, IBM Security highlighted some scary information surrounding the threat of ransomware.
Right off the bat, the biggest finding is that ransomware is on the rise. While the original concept dates back to 1989, when a floppy disk containing a “locking code” was snail-mailed to victims, IBM Security noted that ransomware attacks have been increasingly rampant since 2014.
In fact, they noted that “the concept has gained ‘tremendous momentum’ with improved encryption capabilities exploited by cybercriminals and the growing use of cryptocurrency like Bitcoin,” or the underlying blockchain technology. But one-step “ransomware attacks quadrupled in 2016, with an average of 4,000 attacks per day.”
The FBI even reported back in 2016 that within just the first 3 months of 2016, more than $209 MILLION in ransomware payments have been made in the United States.” In fact, this is a “dramatic 771 percent increase over a reported $24 million” for all of 2015.

The FBI estimates ransomware is currently on the right pace to be around a $1 billion source of revenue for cybercriminals in 2016. And as we saw in May of 2017, the FBI isn’t too far off. So yeah, the threat is absolutely huge. We’re not talking about $20 payments: IBM Security notes that ransoms have been reported as low as $500, but also as high as some cases demanding into the millions. Depending on your business, of course, the ransom might be different — but it will always hurt.
How Does It Work?
Now that we have a basic understanding of what a ransomware attack is, and we know the threat is a very real one, the next piece of the puzzle would be to understand how exactly this type of attack is carried out. After all, you must know your enemy to beat your enemy, and understanding the root cause of ransomware attacks alone can be enough to help prevent them.
Just as I wrote previously in my guide on network security, common sense is the best practice. No amount of security, firewalls or session border controllers will keep an intruder out if someone on the network just opens the door wide and lets the attacker in. This is where the concept of “social engineering” comes in, which involves deceiving and manipulating individuals into either sharing confidential information, or even allow access into otherwise restricted systems.
Ransomware, like most malicious software attacks, are a bit like vampires — they must be invited in to gain access. While this is not a perfect analogy, it helps get the point across. A computer virus cannot just download itself onto your machine without your consent — there generally needs to be a point of contact — the most common of which is spam emails with attachments, which IBM Security has also noticed an increase of.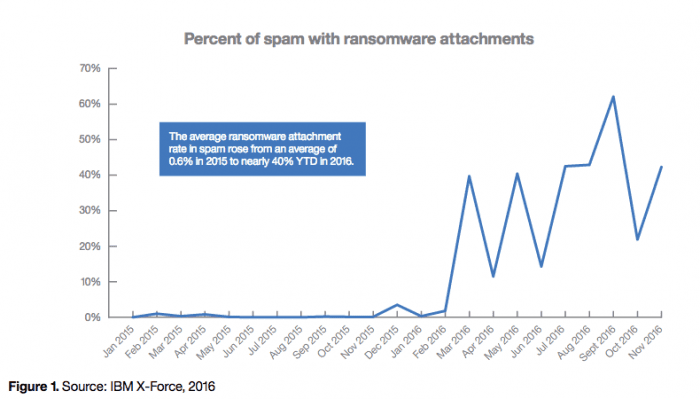
You know that fishy email you got from that address that looks kind of like Becky’s, but has a weird attachment? Don’t open it, don’t download the attachment, don’t even look at it. According to IBM, unsolicited emails and spam are the major cause of ransomware making its way into your network.
Open an email, or download an attachment, and the Ransomware was just given access to your machine. From there, this malicious software can scan file systems on the endpoint, “and find all the locations where the victim keeps files, including shadow copies and backup files as well as network repositories and even external drives attached to the endpoint.”
Once it finds everything, the malware can then jump from one device to every single other one on the network, encryption takes over and locks down your entire system or valuable information, and you now have to pay to get it back. But, this doesn’t exactly tell the whole story. In fact, according to Malwarebytes Labs, WannaCry didn’t even begin from a sketchy email attachment.
How Did WannaCry Spread So Far?
After all, it’s not like 230,000 individuals opened the same email that allowed WannaCry onto their machines. Again, according to Malwarebytes, the idea is that some tricky NSA software and practices were used to find weak spots in networks.
“This nasty worm was spread via an operation that hunts down vulnerable public facing SMB ports, and then uses the alleged NSA-leaked EternalBlue exploit to get on the network and the (also NSA alleged) DoublePulsar exploit to establish persistence and allow for the installation of the WannaCry Ransomware.”
Now, this is a bit technical and if you want to go even further into detail, Malwarebytes does a great job of breaking everything down. However, the important thing to note is that WannaCry didn’t start from an email — so while it’s a major source it’s not the only one, nor is it the most feared. WannaCry was the “vampire” that evolved to find its own unique way into a house instead of needing to be invited in. Oh, and WannaCry used “weaponized” exploits (the EternalBlue and DoublePulsar stuff) from the NSA — that’s also important to note.
Unified Communications and Ransomware
So you may be thinking that ransomware can only be used to lock out your computers to prevent access to files and the devices themselves. Well, that’s one of the largest concerns, but in an ever-connected world of Cloud solutions, it’s not the only concern. In fact, VoIP and Unified Communications specifically have a unique ransomware threat.
During WannaCry alone, hospitals were reporting that not only were computers impacted, but also the hospitals telephony systems. This type of software can spread to just about any connected device or system, including the Unified Communications solutions we use everyday in our business. VoIP attacks are on the rise, and every single desk phone you have hooked up to your network that’s not properly secured allows for extra access points into your network. There are also Skype and Type attacks, in which callers can figure out what you were typing while on the phone to allow them unauthorized access to a network.
Malwarebytes also notes that the WannaCry attack took advantage of specific protocols, specifically the “SMB protocol.” They explain that SMB is used to transfer files between computers, and is a setting most often enabled on devices by default, despite a lack of need for the protocol. Malwarebytes specifically recommends that users disable SMB, “and other communications protocols if not in use.”
Lower The Risk, Protect Your Business
So as any security expert will tell you, the first and perhaps strongest line of defense is simply education. If we are aware of what potential threats lurk around the corner, we are aware of how these threats make their way into our networks and how to prevent these threats from infecting our devices.
But, simply telling your team to not open any sketchy emails isn’t enough. We all make mistakes, and at the end of the day it could be a honest mistake that leads to a massive infection. On the other hand, as we saw with WannaCry, these ransomware attacks are even finding their own way onto computers. So how do we protect against such a massive threat? There are some basic practices we can take into account.
- Update EVERYTHING
Time and again I see people ignoring those update warnings on their phones and computers, and time and again I see issues pop up that were resolved with these latest updates. It may be annoying, it may take some time away from your day, but you need to update your devices. As annoying as it is for Microsoft to force updates onto Windows 10 computers, they have a point. If there is a security flaw, it must be fixed, and those fixes come in those boring computer updates. Hell, just after WannaCry, Microsoft went ahead and patched Windows XP — a mostly abandoned operating system. Keep. Everything. Up. To. Date.
- Back up EVERYTHING
There are two types of people: those who back up their data, and those who haven’t had the traumatizing experience of losing their data. When your business is relying on some critical information inside these systems to stay operating on a day-to-day business, you must back everything up. If ransomware attacks and you can’t get your main system online, you at least have a safety net to fall back on if your backup is up-to-date and secure. Since ransomware can jump from one device to every other device on the same network, backups should be kept in unique, secure locations on secure networks unrelated to the main network infrastructure. Oh, and data is not backed up unless its saved in THREE locations. Redundancy is the key.
- Implement and Maintain Security Software
Though I’ve spoken about security software before, it’s worth mentioning again. The use of up-to-date antivirus and malware detection software installed on all employee endpoints, a direct recommendation from IBM Security, is the best way to start. IBM also recommends you go one step further and set up regular scans as well as automatic updates for all antivirus software. On top of antivirus and detection software, network gatekeepers like the previously mentioned hardware or software firewalls and session border controllers will help keep out unwanted eyes. Consider a VPN for mobile and remote users, as well.
- Create and Maintain an Incident Response Plan
This point coexists with educating and training staff, and should be included in the overall planning when it comes to security. Even with all the measures in place to prevent an attack, chances are that one could still occur. Establish an incident response plan so key teams know how to react quickly to prevent as much damage as possible. Most importantly, in the event of an attack, STOP THE SPREAD. Disconnect all devices, stay off the network, and use mobile or personal devices. A single infected machine that’s kept connected can cause the entire network to become infected within minutes — and this contributes to the security nightmare of a BYoD-only workplace.
- Stop Hoarding Exploits
This of course won’t apply to every, or even many, businesses at all. But at the end of the day, we need to stop hoarding potential exploits and known malware in an attempt to “weaponize ” these tools. This was a strong point made by Microsoft President Brad Smith, and one worth echoing. NSA weaponized exploits were allegedly used in WannaCry, and of course could be used again and again.
A Real Threat That Isn’t Going Away
As we can plainly see, ransomware is without a doubt a huge threat. And, as we can also plainly see, ransomware isn’t going away any time soon. In fact, we could more likely expect to see a rise in ransomware attacks within the next few years, as we have already seen since 2014. Unfortunately, there is no perfect defense, but preparing for disaster in any way is better than waiting around for something to happen first.
If WannaCry isn’t the wake-up call your business needs to take security seriously, then hopefully it won’t be too late once another massive attack occurs. We already saw one exploit reach 230,000 computers around the world — who knows how massive and detrimental the next attack could be?