We’ve talked about trends quite a bit before, looking at both 2017 UC trends and even 2017 team collaboration trends. One massive trend we haven’t focused on yet, though, is the adoption of BYoD policies. As the concept of mobility becomes more desirable within the workforce, the concept of bringing your own device to work makes a whole lot of sense.
Of course, one of the most obvious benefits is the reduction of cost for employers, who no longer have to pay for their teams’ secondary mobile phones or workstations. Believe it or not, though, economization is not the main reason why more companies are adopting this policy. Employee satisfaction, mobility, and productivity are the three biggest benefits of BYoD.
However, at the same time, the downsides are equally glaring. It makes sense why a business would hesitate to adopt this approach since security and privacy are the biggest concerns. We recently took a look at the Crowd Research Partner’s BYoD Spotlight Report, which highlights the concerns and benefits of this kind of policy. We wanted to expand upon the report, share our major takeaways, and offer insight as to how your business can best secure its network while moving towards a bring-your-own culture.
Is The Risk Even Worth It?
If your business has operated without the BYoD approach for many years, you’re probably thinking, “Why bother?” Is the increased possibility of a security breach really worth giving your team members the freedom to use their own phones? Though we’ve highlighted the pros and cons of BYoD in the past, it’s worth looking at again. After all, many think that this approach, if anything, promotes the concept of shadow IT — the concept of employees adopting their own solutions without consulting IT. Without a doubt, the biggest resistance of adopting of these policies stems from security concerns.
This can lead to compatibility issues, collaboration road blocks and, of course, security concerns. For example, Cisco Spark is an amazing choice for any team that wants intense security. Slack, on the other hand, is less than stellar when it comes to security. This shortcoming has caused an explosion of security-focused Slack alternatives. All of your secure communications go out the window as soon as one team decides to use Slack over Spark, even though the other teams use the latter.
Crowd’s research concluded that “12.1 billion mobile devices will be in use by 2018; half of the globe’s employers require BYOD by 2017; 67 percent of CIOs and IT professionals are convinced that mobility will impact their organizations as much, or more, than the Internet did in the 1990s.”
Realistically, the benefits your team can gain from these policies can outweigh security concerns. Crowd noticed that a BYoD approach provides:
- Increased mobility
- Improved employee satisfaction
- A large productivity boost
- Cost savings, of course
Now, satisfaction may seem like a superficial measure at first, but it has been proven time and time again that happy workers are productive workers. As I’ve said in the past, user experience is key — if an application or solution is complicated, no one will use it. Forcing your employees to use the same, possibly outdated devices can lead to upset employees fighting the technology more often than getting work done. Below are the results of a survey in which businesses were asked what they felt would be the biggest benefit of this kind of policy:
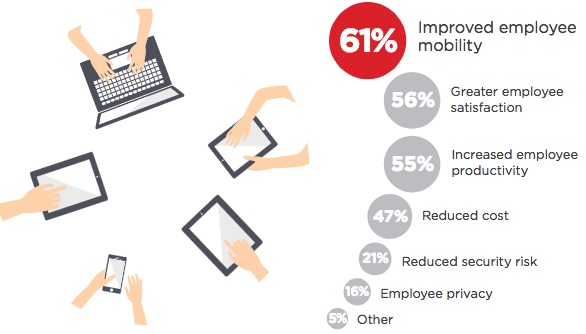
It is worth noting that these percentages do not add up to 100% because some businesses who participated in the survey selected multiple aspects. This only further highlights the benefits of a BYoD approach.
So, if you’re looking to be a cutting-edge business and leverage any possible advantage, it’s safe to say that embracing the bring-your-own approach would allow your workers to focus on their work. This leads to happy, productive, and accomplished teams.
Risks To Consider
As we touched upon previously, the major risks associated with a BYoD approach concern security and privacy. Those are both very incredibly broad topics, but it’s possible to condense the two. Allowing competitors access to your company’s metaphoric secret vault is one glaring example. Thus, every business should plan out their BYoD approach the right way. Malware, in general, is a major concern. In fact, 39% of businesses surveyed said they found a BYO device on their network that had downloaded Malware.
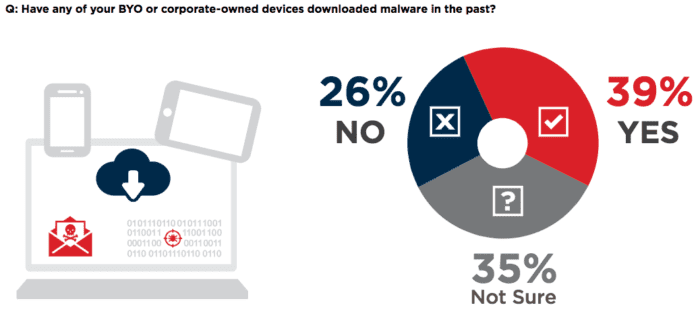
The risk of ransomware attacks are also a growing concern. These are attacks in which hackers make their way into your network to either shut it — or parts of it — down, or gather information and hold all of it hostage. These attackers force your company to pay a pretty penny to get your stuff back. However, no matter the attack, the vast majority of businesses claim security concerns as being their biggest BYoD barrier.
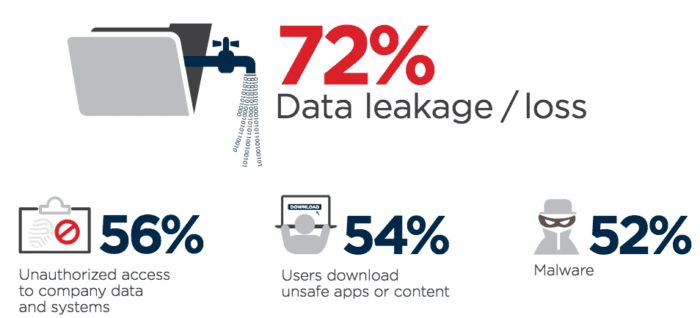
Specifically, what businesses fear most are data leakage and data loss. The idea of allowing unauthorized persons to access your business’s crucial, private information is a big hurdle to overcome. Such risks include:
- Data leakage or data loss
- Unauthorized access to company data and systems
- Users download unsafe apps and access unauthorized content
- Malware and other infectious software, such as the previously mentioned ransomware
- Lost and stolen devices
- Vulnerability exploits in unsecured devices
- The inability to control endpoint security
- Ensuring up-to-date security software on every device
- Regulation compliance
- Network attacks via unsecured WiFi
Beyond security concerns, most businesses cite integration as being the second biggest hinderance. Integrations let us do things like reconstruct Slack to suit remote workers. We all know how important integrations are. Businesses surveyed said that a mobile security solution that can integrate into their existing network and application stack is a high priority.
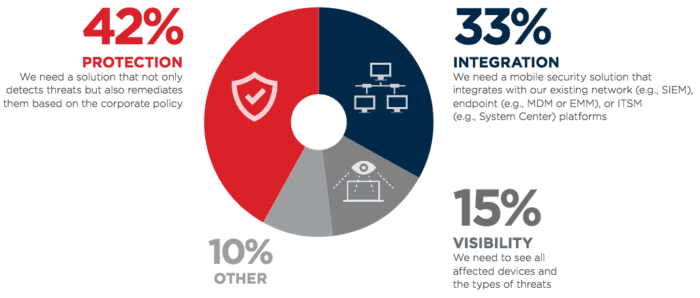
Businesses are also concerned with the network visibility of any threats or compromised devices. In fact, 35% of businesses reported that BYoD required additional IT resources to manage mobile security. This represents a very good point: security can be expensive, time-consuming, and detract from your business’s higher priorities.

As we take a look below, though, you’ll see that protecting your BYoD applications and network doesn’t have to be complicated.
Take Control and Secure Your BYoD Network
A BYoD office doesn’t have to mean a black hole of security nightmares. (We’ll leave that to the IoT.) Just as we discussed with protecting your VoIP network, the simplest security policies and practices will help keep everything locked down. Now, common sense is ultimately the best defense when it comes to keeping your data safe. Thus, first and foremost, make sure your bring-your-own teams have as little room for error as possible.
Establish Proper Security Practices and Protocols
I’m not talking about protocols like SIP and H.323, which let your VoIP service exist, but good old-fashioned guidelines. Without a doubt, the biggest risk in this approach will come from not regulating how teams function and utilize their personal devices. Just like anything else in life, ignoring the problem won’t make it go away.
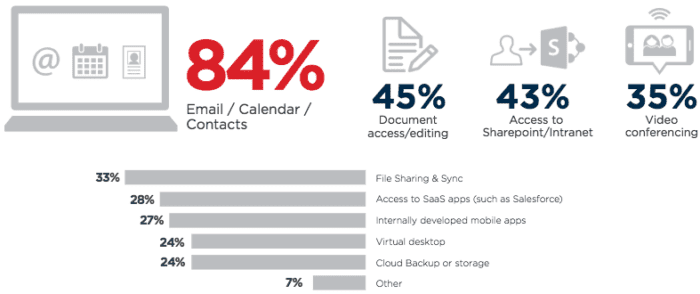
Above is another set of survey results in which businesses ranked their ideal functions of a BYO device, and what they would allow their teams to use their devices for. These aspects are important to take into account when considering policies, guidelines, and approved applications or functions. Generally, the rules and regulations your business (specifically your IT department) chooses to enact should vary based on these specific team functions and roles.
Accepted Use Guidelines:
Start right at the beginning. Determine what does and does not qualify as accepted use for your team. Clearly define acceptable business use with specific activities that directly or indirectly support your business. Limiting, but not outright banning, personal communication could help establish how your employees should view BYoD.
Of course, limiting web access makes for a good start; however, studies have shown that leisurely web browsing can be beneficial for productivity, so don’t go overboard. More importantly, limit how and when your teams can store or transmit sensitive information over their mobile devices. Routine security checks are a great policy to ensure each device is up to date and compliant with guidelines.
Criteria For Allowed Applications:
It’s impossible to ban all apps and prevent your teams from installing their favorites on their personal devices. That said, provide criteria for what should be utilized for work, and attempt to set consistency across the board. As we discussed previously, shadow IT can be a big problem.
Ensuring all of your communications occur over the same platform is important in security maintenance. It’s also possible to simply disallow apps that are not from highly regarded providers, like Google Play or the Apple App Store. Some devices even allows IT to enable or disable app downloads from unofficial locations.
Employee Departure Practices:
When an employee leaves the team, their device may still contain all of their previous business-related information, data, communications, and files. The first step your business can take is to establish a policy for departing employees. A departing employee policy is one of the best security practices your business can employ.
It’s not realistic to ask departing employees to wipe everything off their personal device, but removing at least all business communications and applications makes sense.
Password Policies:
Most people take passwords for granted — they reuse whatever is easiest for them to remember. We could go into a whole discussion on the best password practices, but that’s another topic for another day. Suffice to say that a simple way to stay on top of passwords is to establish a limited time policy.
At a minimum, your policy should require employees change their passwords routinely, and require a strict set of password requirements to prevent simple brute-force attacks.
Routine Security Checks:
It’s one thing to employ a set of guidelines and policies, but it’s another thing to enforce them. After all, what good are your rules if no one is following them because no one is enforcing them? A large business with the luxury of an IT department will have the benefit of a team dedicated to ensuring the best security measures.
Realistically, though, any sized business can and should establish simple security checks. Once a month, gather your team to reset passwords and review your policies. Analytics alone can help your business by, for example, improving your VoIP call reports. Below, we discuss the available tools for powerful audit reports, which include logging, monitoring, and remote access.
Deploy and Utilize The Right Set of Tools
It would make sense to follow up with the right set of tools for the job if your business is going to establish proper use policies.
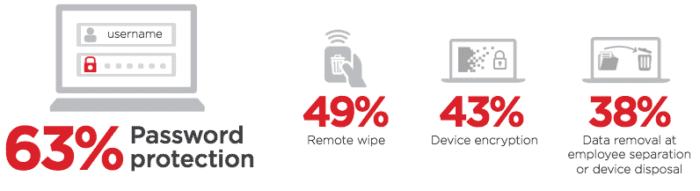 This is a broad idea, but utilizing enterprise-focused solutions will help minimize both security risks and compatibility issues between teams. Mobile device management solutions are the easiest ways to get everything under one roof. However, your business doesn’t need to shell out to keep your network secure with the right policies. These could also be classified as Risk Control Measures.
This is a broad idea, but utilizing enterprise-focused solutions will help minimize both security risks and compatibility issues between teams. Mobile device management solutions are the easiest ways to get everything under one roof. However, your business doesn’t need to shell out to keep your network secure with the right policies. These could also be classified as Risk Control Measures.
Mobile Device Management:
Now, these solutions are in a class of their own. Generally focused on the enterprise market, they might be out of reach for some smaller teams that are just using their personal phones and computers. However, if your business wants to take security as seriously as it should, then investing in the right solution can go a long way.
These tools can be used to automate the process of removing business data from a user’s phone. They can even set “geofencing” rules, which limit where users can access their business apps or accounts. Some popular solutions include SOTI MobiControl, Vmware AirWatch, Citrix XenMobile, and Microsoft Intune.
Data and Device Encryption:
As we previously noted, not every business will feel the dire need to invest in an enterprise solution, but that doesn’t leave them without any alternatives. It is possible to piece together a secure solution on your own by utilizing the right methods of communication and the most apps as possible.
I’ve noted multiple times how secure Cisco Spark is, but just to emphasize again: Cisco can’t even see your communications. You can ensure proper device encryption a number of different ways, but one of the most affordable and obvious is to set up a Virtual Private Network (VPN) — something every business should have.
Remote Device Access:
Remote device access exists as a category of its own, and can be utilized for a number of different scenarios. If your mobile employees require support or assistance, remote device access applications are a godsend for IT teams. These can also be used to ensure security and help remove data from departing employees, or ensure teams are following proper guidelines.
These tools can also assist in routine security checks if that is a policy your business would like to deploy. Remote wipe tools are common as well, and the two can generally be classified the same category.
Two-Factor Authentication:
Should your business choose to use it, two-factor authentication would work hand-in-hand with your VPN. Two-factor authentication is one of the simplest ways to secure your accounts and devices even further. Think of this as the dead-bolt lock to a front door. Two-factor authentication requires users to identify themselves by a second measure beyond their password. In fact, Twilio and Nexmo are two of the most popular platforms that make this possible.
How users identify themselves depends on application and use case. However, it commonly involves sending a time-limited code via phone call, text message, or email. Some businesses may even go the extra mile and equip their teams with “authenticator” keychains — which generate a random number string every time a user logs in or establishes a VPN connection.
Firewalls and Anti-Virus:
We took a look at the difference between software and hardware firewalls before, and want to stress again how crucial these tools are to securing your network. While it may not be possible to install a software firewall on every team member’s BYoD mobile phone, protecting your network with either a hardware firewall or even a Session Border Controller is one of the best ways to lock down your entire network.
If your business uses a firewall as a first and second line of defense, it will also be configured with a VPN. These tools can also help prevent the dreaded DDoS attacks that bring even the biggest networks to their knees. Antivirus solutions are another similar tool that generally work hand-in-hand with a proper firewall setup, and should be utilized on all devices, where possible.
BYoD Is Here To Stay
If your business is looking to gain any sort of advantage, BYoD is definitely worth considering. As we have seen, the vast majority of businesses utilizing this policy see the benefits outweighing the concerns. Security is incredibly important for any business, and I’ve said time and time again that everyone needs to take it seriously.
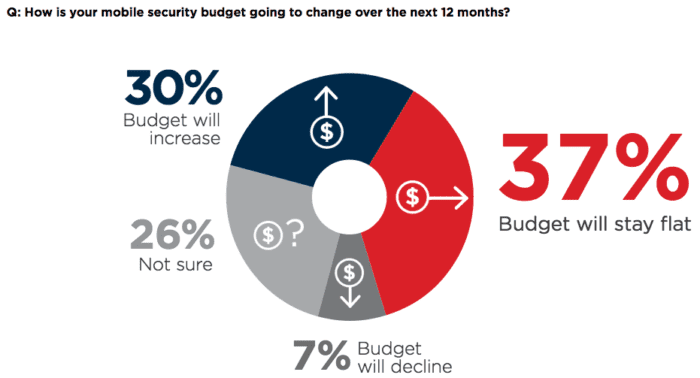 However, that doesn’t mean your business cannot leverage a BYoD approach. Common sense measures alone will go a long way in keeping your data locked up. It really only takes a small investment, both in time and money, to employ simple security practices. While 30% of companies saw their budget increase, even more saw their budget stay flat, and 7% saw it decrease. Overall, BYoD is one of the biggest UC and workforce trends that is growing alongside the concept of mobility we now treasure.
However, that doesn’t mean your business cannot leverage a BYoD approach. Common sense measures alone will go a long way in keeping your data locked up. It really only takes a small investment, both in time and money, to employ simple security practices. While 30% of companies saw their budget increase, even more saw their budget stay flat, and 7% saw it decrease. Overall, BYoD is one of the biggest UC and workforce trends that is growing alongside the concept of mobility we now treasure.
Just about every contemporary provider is focused on mobility, and every business should recognize the benefits it could bring to the table. The current state of BYoD should be focused on growing adoption but, more importantly, security. Businesses have a right to be concerned about security, but they should also recognize how simple it could be to keep everything secure. Don’t let the fear of a back-door hack keep your business from making the right decision and employing the right policies for your team.