VoIP phone systems offer countless benefits to large and small businesses like streamlined communications, faster customer service resolution rates, and increased productivity.
But is VoIP secure?
In this post, we’ll outline why VoIP security matters even if you have “nothing to hide,” the role that call encryption plays in creating a secure environment, the top VoIP security vulnerabilities, and what security administrators can do to ensure your business is protected against them.
Even if you can’t entirely eliminate the global threat of cybercrime, increasing awareness of and protection against VoIP security issues can seriously mitigate your risk.
Table of Contents:
- Why is VoIP Security Important?
- Is VoIP More Secure than Landlines?
- What is VoIP Encryption and How Does it Work?
- Types of VoIP Security Risks and How to Prevent Them
- How to Tell if your VoIP Provider is Secure
- VoIP Security Best Practices For IT Leaders
- The Most Secure & Encrypted VoIP Providers
- VoIP Security FAQs
Why is VoIP Security Important?
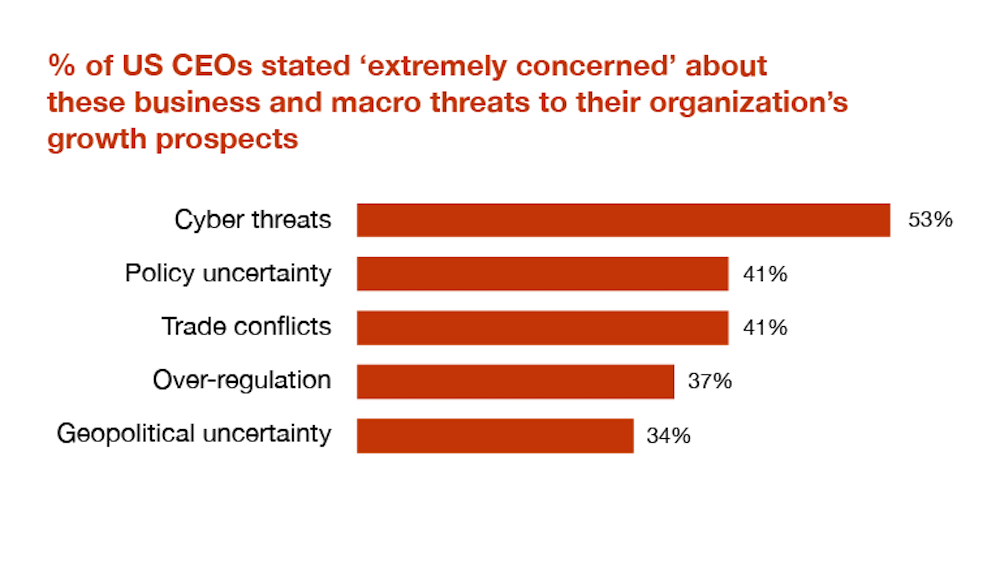
Close to 70% of top business decision-makers believe they’re experiencing a major increase in cybersecurity risks. In fact, most CEOs state they’re ‘extremely concerned’:
Businesses focused so much on quickly adapting to the “new normal” of a remote and blended workforce that VoIP security became more of an afterthought than an up-front consideration. (The sudden rise of Zoombombing at the start of the pandemic perfectly illustrates that.)
Unfortunately, many businesses did not see why VoIP security mattered — and the disastrous impact of data breaches and other cybercrimes — until it was too late.
So, why should you care about VoIP security?
Small Businesses Are The Primary Target
Over half of small businesses suffer from data breaches or other cyber-attacks every year.
Why?
Because hackers know that most small businesses don’t have an adequate security strategy — if they have one at all — in place. Roughly 43% of all cyber-attacks and 95% of credit card breaches are on small businesses, but only 14% of those businesses have the security measures in place to withstand them.
Plus, 35% of businesses haven’t even reviewed or updated their security strategies since they were put into place.
Cyber Attacks Have Serious Financial Consequences
The average cost of a data breach was $3.86 million in 2021 — and things will only go up from there.
Even if your business doesn’t have to fork over that much, you’ll still lose the majority of your profits.
There are the more obvious things like legal fees, lawsuits, and audits, and then there are hidden costs like lost work time, a loss of customers, and network downtime.
Small businesses see disastrous financial consequences, as well, with data breaches costing roughly $3,533 per employee.
Many Businesses Don’t Recover From Security Breaches
Still think you can “bounce back” from a data breach?
The reality is that over 60% of small businesses are forced to close their doors for good within six months after a cyber attack.
Even if all of your data is “backed up” and “recovered,” you’ll still be facing major damage that could financially destroy your business.
And, even if you can pay the fines and stay open, there might not be enough business to keep things that way. Studies show that retailers who have experienced a cyber attack have underperformed by over 15% even three years after the initial incident. Major companies like Target, who saw their consumer perception drop by roughly 54% a year after their infamous 2013 data breach, have trouble recovering.
So, while some major retailers and well-known brands can recover from a data breach, your small business probably won’t be so lucky.
Over-Reliance on the “Nothing To Hide” Myth
Many businesses operate under the mistaken assumption that a data breach won’t be a major issue, as they have “nothing to hide.”
Just because you don’t have any scandalous emails or shady backdoor dealings, this doesn’t mean that you won’t be targeted and gravely impacted by a cyber attack. No one is immune to cybercrime, nor to its consequences. But most of all, having “nothing to hide” is a myth.
Using the same passwords for business accounts as you do for your personal accounts? Have you saved your credit card information to make for a faster checkout? Pre-filled your personal contact information, like your home address and phone number? And what about those synced devices, company reports, taxes, invoices, and more?
By ignoring VoIP security, you’re also willingly putting your clients’ personal information and data at risk of being stolen or publicized. This will hurt both consumer trust in your brand and your company’s pockets (hello, lawsuits!)
Being proactive about VoIP security, and recognizing it for the serious threat that it is, will keep you, your employees, and your customers safe and secure.
Is VoIP More Secure than Landlines?
When configured correctly, yes, VoIP phones are generally more secure than landlines.
To better understand the answer, consider the differences in how virtual phones vs landlines transmit and store data.
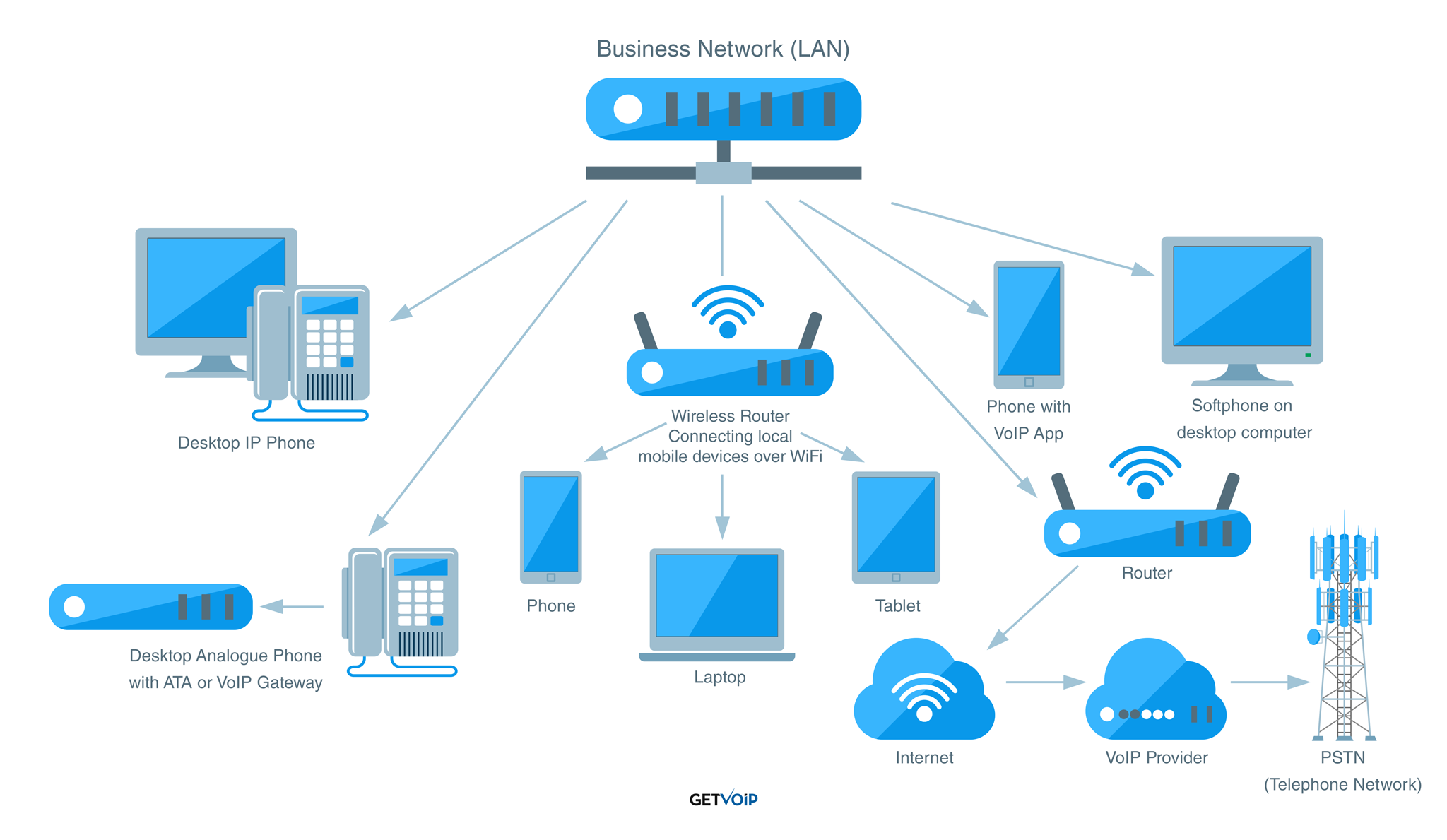
Traditional analog phones make and receive calls through the PSTN network made up of copper wires and fiber optic cables. In other words, there’s a physical connection between the caller and the recipient (outlined in the diagram below.
VoIP transmits data over the Internet, making digital calls via packet switching.
In packet switching, voice data is broken up into smaller packets, which are then sent over the Internet connection to the receiving end of the line. There, they reconnect and successfully transmit voice data.(Outlined in the diagram below.)
To access landline phones, eavesdroppers hack into the wires/cables (AKA, “wiretapping.”) Guarding against this is not only more difficult on landline phones than with VoIP, but also much more expensive.
Landline security is severely limited by its lack of technology and monitoring capabilities — which VoIP systems have in droves.
So while on paper, landlines may seem more secure, VoIP systems actually offer a higher overall level of security as long as you’re using the tools it provides — like VoIP encryption.
What is VoIP Encryption and How does Security Differ?
VoIP encryption is the process of scrambling voice data packets into unreadable jumbles while they are in transit, preventing them from being intercepted or deciphered by hackers.
Even if a hacker somehow intercepts the call, encryption ensures they won’t be able to make sense of anything they discover.
To understand how encryption works, we need to take a closer look at the transmission process.
When voice data packets are transferred from the sender to the recipient, they use an IP transport protocol called the SRTP (Secure Real-Time Transport Protocol.) SRTP is a cryptographic protocol that applies the Advanced Encryption Standard (AES) to data packets, provides message authentication, and offers additional protection against potential replay attacks.
In addition to SRTP, VoIP providers use another form of encryption called Transport Layer Security (TLS) or SIP over TLS to protect additional call information.
TLS scrambles data like phone numbers, the names of callers, usernames, and more. It also works to stop message tampering and call eavesdropping.
Remember that quality providers should offer both TLS and AES Encryption.
What is End-To-End Encryption?
You’ve probably heard the term “end-to-end encryption” a lot when researching VoIP security.
Standard TLS encryption includes only client-to-server encryption or C2S.
If a hacker breaks into the C2S server, they’ll have access to all of your network’s data and communication. Access to the C2S server means hackers can eavesdrop on and record calls, manipulate files when they’re being transferred, and see all of your company’s message history.
End-to-end encryption (E2EE) directly encrypts communication between users, meaning that the only people who will be able to access calls and messages are the senders and recipients. When you make a call, the data packets at your end are encrypted when sent and are only decrypted once they reach the recipient.
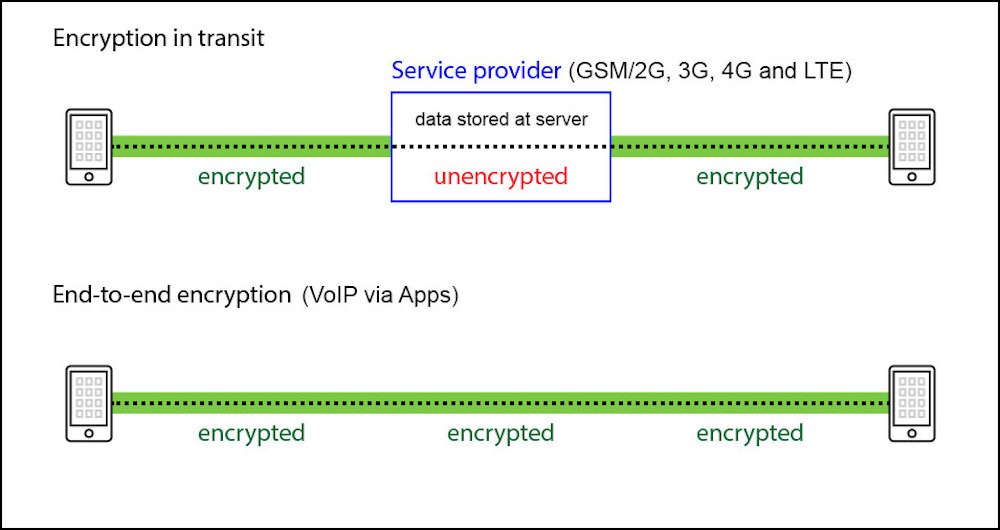
Servers, ISPs, hackers, and telecom providers won’t be able to access your communication, as long as it’s end-to-end encrypted.
Check to ensure that you’ve enabled end-to-end encryption before you begin communication on your VoIP system. Some providers, like Skype, don’t make end-to-end encryption the default option, leaving you vulnerable to hackers and attacks.
Types of VoIP Security Risks and How to Prevent Them
No device — whether it’s your smartphone, a softphone, or an IP desktop phone — can ever be 100% protected from all security threats. Here are the basics:
But by identifying the most common VoIP vulnerabilities and working to prevent and respond to them, you can ensure they don’t destroy your business. Softphones, and smart devices all present potential vulnerabilities for VoIP.
Below, we’ve outlined the most common VoIP security risks along with tips on how to stop them from destroying your business.
Packet Sniffing and Black Hole Attacks
One of the most common VoIP attacks is called packet sniffing, which allows hackers to steal and log unencrypted information contained in voice data packets while they are in transit.
Packet loss, when voice data packets don’t reach their destination, is caused by packet sniffers looking to steal information and slow service via a packet drop attack (sometimes called a black hole attack.) These packet sniffers intentionally drop packets into data streams by taking control of your router, resulting in a much slower network service or a complete loss of network connection.
Packet sniffing also makes it easy for hackers to intercept usernames, passwords, and other sensitive data.
To help make your Internet lines more secure, use a reliable VoIP VPN option or a virtual private network to send information. This takes some time to set up and get running, but it ensures that information is secure.
Users can also guard against packet sniffing and black hole attacks by ensuring all data is end-to-end encrypted and through consistent network monitoring, which will instantly alert users to suspicious login attempts, unfamiliar devices, and more.
DDoS Attacks
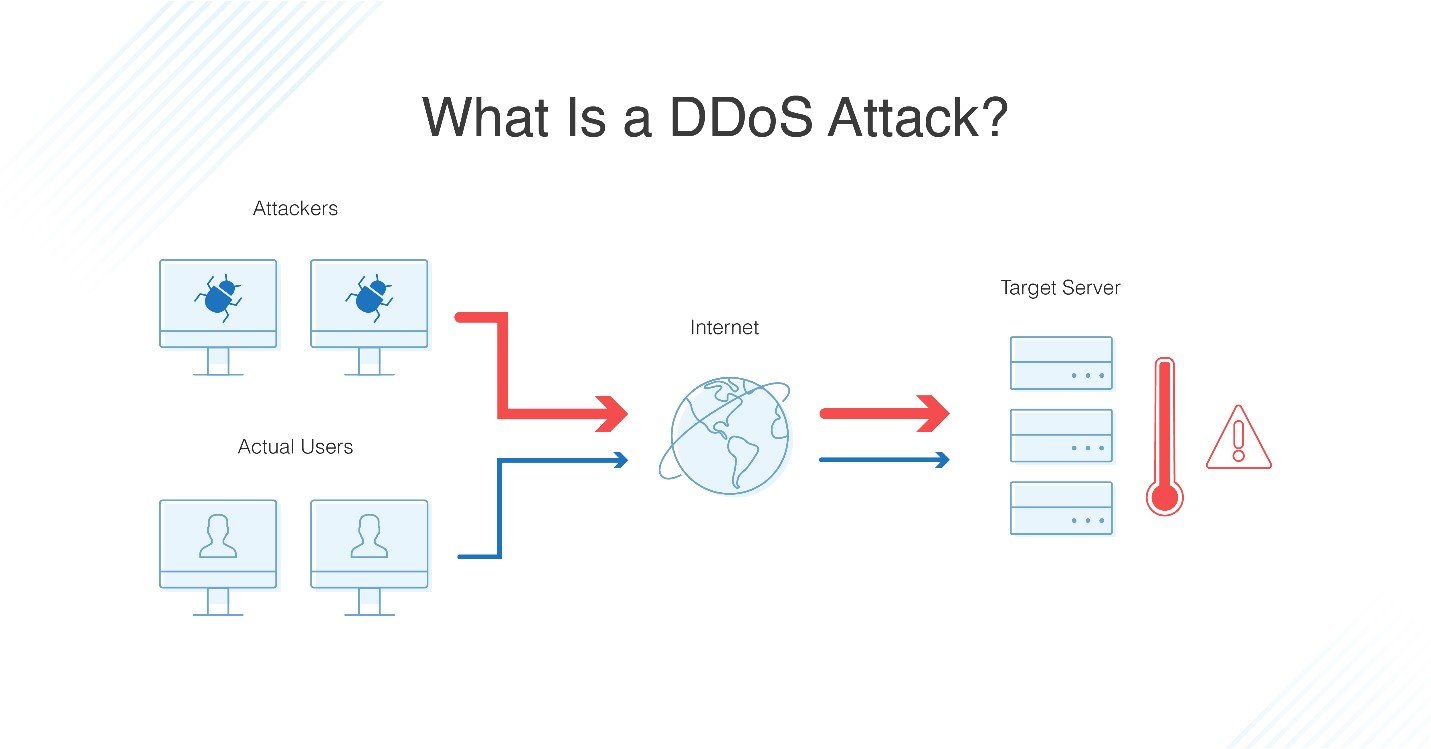
DDoS (Distributed Denial of Service) attacks, as the name suggests, make it impossible for businesses to use their own VoIP services by intentionally overwhelming servers.
Usually, these DDoS are caused by a network of botnets, which are remotely-controlled computers/bots that hackers have manipulated. These “Zombie Computers” flood networks, websites, and servers with much more data or connection requests than they’re able to handle, rendering VoIP services inoperable.
Common signs of a DDoS attack include:
- Unusual and prolonged bandwidth spikes
- 503 HTTP Error Responses
- Slowed service
- A sudden surge in traffic from similar devices, IP addresses, or locations
To mitigate DDoS attacks, use a separate, dedicated Internet connection just for VoIP. VLANs (Virtual Local Area Networks) specifically provisioned for VoIP traffic are an excellent option here, in no small part because it makes it much easier to recognize unauthorized or unfamiliar data flows. For VoIP users sharing across a wide area network (WAN), managed encryption is the best way to guard against DDoS attacks.
Vishing

Vishing is VoIP-based phishing, meaning that a hacker pretends to call you from a trusted phone number or source with the intent of getting you to reveal sensitive information to them, such as passwords, credit card numbers, and more.
Caller ID spoofing – the process where these vishing hackers make the names and numbers that appear on your caller ID seem legitimate — intentionally confuses potential victims. These hackers may appear to be calling from your bank’s phone number, claiming that your account has been compromised, and requesting your password so they can secure it immediately.
To prevent vishing, targeted agencies should verify all phone requests, even if they seem to come from the organization’s IT department. Agents also need to be trained to refuse to disclose sensitive information unless cleared by the supervisor.
Likely signs of a vishing attack include:
- Extreme urgency/pushiness from the person on the other end of the line
- The hacker keeps requesting that you verify the information by providing it
- Unexpected calls from known numbers or well-established companies
- Short and unusual phone numbers on call screening Caller ID display
To prevent vishing attacks:
- Avoid providing information over the phone to anyone claiming to be the IRS, Medicare, or Social Security Administration (they do not initiate contact)
- Join the Do Not Call Registry
- Don’t respond to voice prompts via voice answers or touchtones
Malware and Viruses
Malware and viruses impact internet-based applications like VoIP, creating a multitude of network security issues. These damaging programs specifically consume network bandwidth and add to signal congestion, which causes signal breakdown for your VoIP calls. These also corrupt data being transmitted across your network, which means that you’ll experience packet loss.
Malware and viruses do a lot of damage by themselves, but they also contribute to future vulnerabilities by creating Trojan backdoors.
These backdoors leave gaps in your security that future hackers exploit to call tamper or steal information relayed in your calls.
To prevent malware and viruses, employ data security measures like encryption and regularly check for network infection. Some routers actively block malware, even going so far as to block dangerous sites from your network.
Most of all, implement VoIP-compatible software and hardware firewalls that scan information to make sure it’s secure.
Phreaking Attack
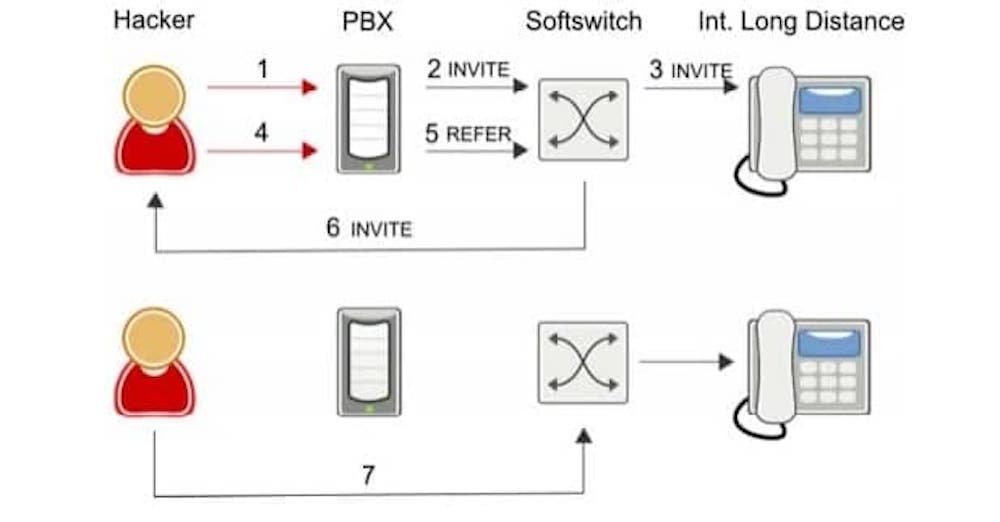
A phreaking attack is a type of fraud where hackers break into your VoIP system in order to make long-distance calls, change calling plans, add more account credits, and make any additional phone calls they want — all on your dime.
These hackers can also steal your stored billing information, access your voicemail, and even reconfigure call forwarding and routing strategies.
They do this by calling your phone system and entering a PIN Number to access an outside line, which allows them to make calls and charge them to you.
If you notice a sudden increase in your phone bills, excessive unknown numbers in your call history, or calls made during off-hours, you may have been the victim of a phreaking attack.
The best way to prevent phreaking is to encrypt all SIP trunks, change account passwords frequently, purchase ransomware protection software, and if possible, avoid saving billing information in the system.
SPIT
SPIT, or Spam over IP Telephony, is similar to phishing attempts and other spam in emails.
SPIT contains prerecorded messages that are sent on VoIP phone systems. These calls are mostly a nuisance that ties up your virtual phone numbers, but the spam carries other risks with it, such as viruses, malware, and other malicious attacks.
A solid VoIP solution helps to ensure that the spam is not damaging to your phone system.
There’s not a way to prevent SPIT entirely, but having a firewall helps identify the spam when it arrives and controls it so that it doesn’t overwhelm your system.
Man-in-the-Middle Attacks
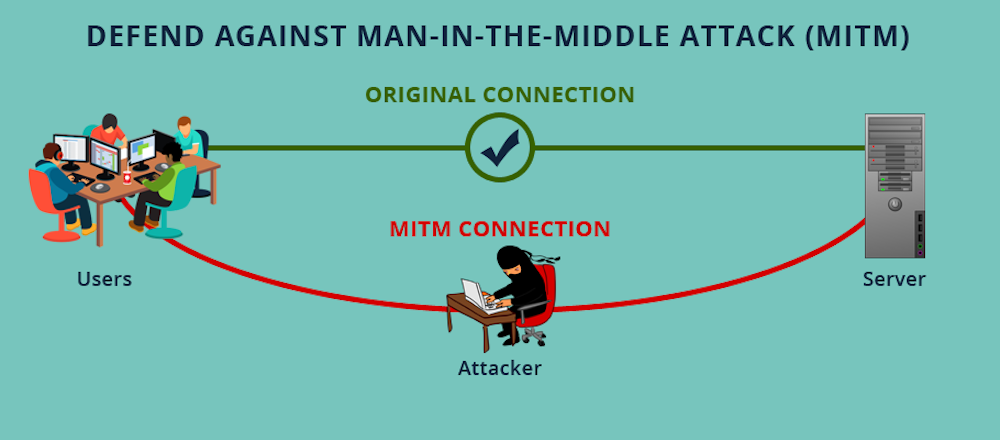
As the name suggests, man-in-the-middle attacks occur when a hacker inserts themselves in between your VoIP network and the call’s intended destination.
This usually happens on public and unsecured WiFi networks. Hackers can easily intercept the call and reroute it through their own servers instead, where they can easily infect it with spyware, malware, and viruses.
The real issue with these attacks is that they can be quite difficult to detect, and even methods like tamper detection or authentication attempts don’t always work.
In addition to avoiding public WiFi, users can prevent man-in-the-middle attacks by having strong WAP/WEP encryption on access points, improving router login credentials, using a VPN, and more.
Toll Fraud
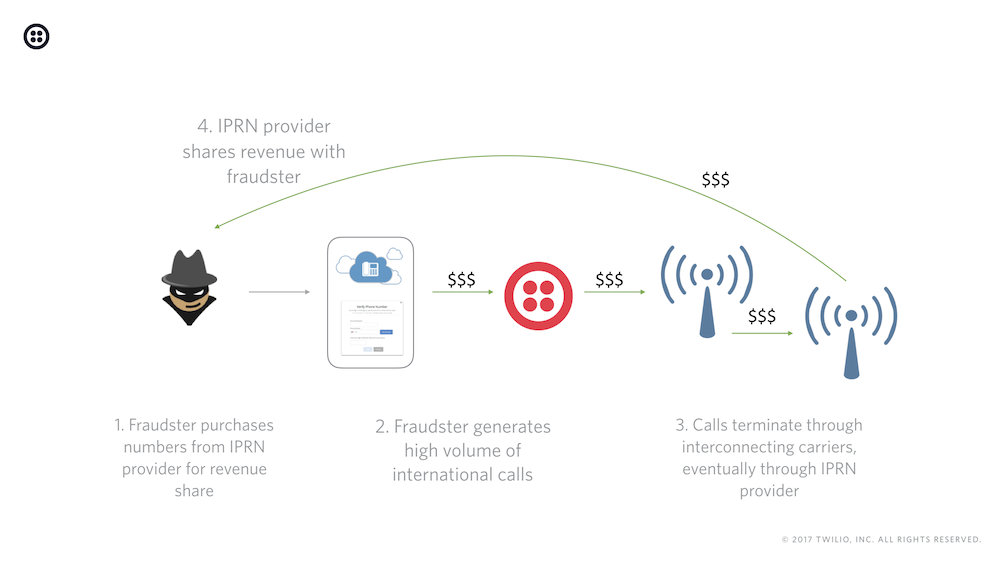
Toll Fraud is somewhat similar to a phreaking attack, but here, hackers intentionally make an excessive number of international calls from your business phone system so they can get a portion of the revenue the calls generate for themselves.
Sometimes known as International Revenue Sharing Fraud, (IRSF) it costs businesses roughly $10 billion every year.
But how do these hackers actually make money?
International premium rate number (IPRN) providers buy and resell phone numbers from carrier groups or country regulators. The hackers then generate a high number of international calls through those numbers, taking their cut through the IPRN.
To prevent toll fraud, enable two-factor authentication on your accounts, restrict geo-permissions by only allowing users to contact certain countries, and set rate limits on things like concurrent calls and call duration.
Call Tampering
Call tampering may not be as severe of a cyber attack as some of the others on this list, but it still seriously limits the way you can do business.
Call tampering is when a hacker injects additional noise packets into the call stream, instantly destroying the call quality and forcing both parties to hang up. These hackers can also prevent packets from being delivered to their proper destination, which makes for spotty, garbled service and long periods of silence.
To prevent this, enable end-to-end encryption, use TLS to authenticate data packets, and use endpoint detection software.
VOMIT

Voice over Misconfigured Internet Telephones, or VOMIT, (gross, we know) is a VoIP hacking tool that actually converts conversations into files that can be played anywhere, making it easy to siphon information from your business phone system.
This type of eavesdropping not only takes data from your system, but also helps the attacker gather business data, such as the call origin, passwords, usernames, phone numbers, and bank information.
To prevent VOMIT, use a cloud-based VoIP provider that encrypts calls before they are sent.
This is especially useful for healthcare companies that require VoIP encryption to make a system HIPAA and HITECH compliant. Follow guidelines from VoIP providers so your system stays compliant with today’s communication infrastructure, and create a private PBX network, as it’s far more secure than a public network.
How to Tell if your VoIP Provider is Secure
Now that you know the risks to look out for, you need to ensure you’ve chosen a high-quality VoIP provider that takes security and user privacy as seriously as you do.
The below list of questions will help you to determine the strategies and levels of security a cloud communications system has in place.
When you talk to your VoIP provider, ask them the following questions:
- What is the guaranteed uptime, and what do you do to minimize downtime?
Look for uptime of at least 99.99% — and get it in writing. You should also take a look at the provider’s Status Page, which shows you historical system outages, network issues, system upgrades, among other incidents.
- How long does it take you to respond to a security breach, and how long does it take to restore safe service?
Make sure you have a solid understanding of how exactly the provider responds to a threat like an attempted eavesdrop or a DDoS attack. What sort of preventative measures do they take? For example, do they send you real-time alerts in the event of a suspicious login or unusual activity? How often do they back up your data to ensure that you have a copy of it in the event of a major attack? How long will it take to restore your service? How long does it take them to respond to an attack?
- Are you GDPR, HIPAA, and PCI compliant? What other security certifications do you have?SOC (Service Organization Compliance) 2 Compliance is one of the most basic must-haves. It was created by the American Institute of CPAs to clearly define criteria for secure data management. It’s made of 5 primary components: security, processing integrity, privacy, availability, and confidentiality.PCI Compliance (Payment Card Industry) is required for any business that accepts payment via card. It ensures that the provider uses secure VLANs, requires frequent penetration testing to protect your IP address, and keeps your system up-to-date.HIPAA compliance ensures that patient health data is properly secured, whether it’s being stored on a cloud-based platform or in relation to call recordings and voicemail.Companies should also have ISO/IEC 20071 certification, which ensures that the provider has strong and current security controls in place.
- How do you physically protect your servers, and what additional measures do you take to mitigate security risks like DNS attacks, phishing, toll fraud, and more?
- If your software uses third-party applications or services, how do you ensure they are following the required security protocols?
- How do you encrypt your data, and does that encryption impact call quality?
- What kind of customer support is available, and what are support hours? (Phone, online live chat, email, etc.)
VoIP Security Best Practices For IT Leaders
Before looking to mitigation and preventative measures, IT leaders should ask themselves these questions:
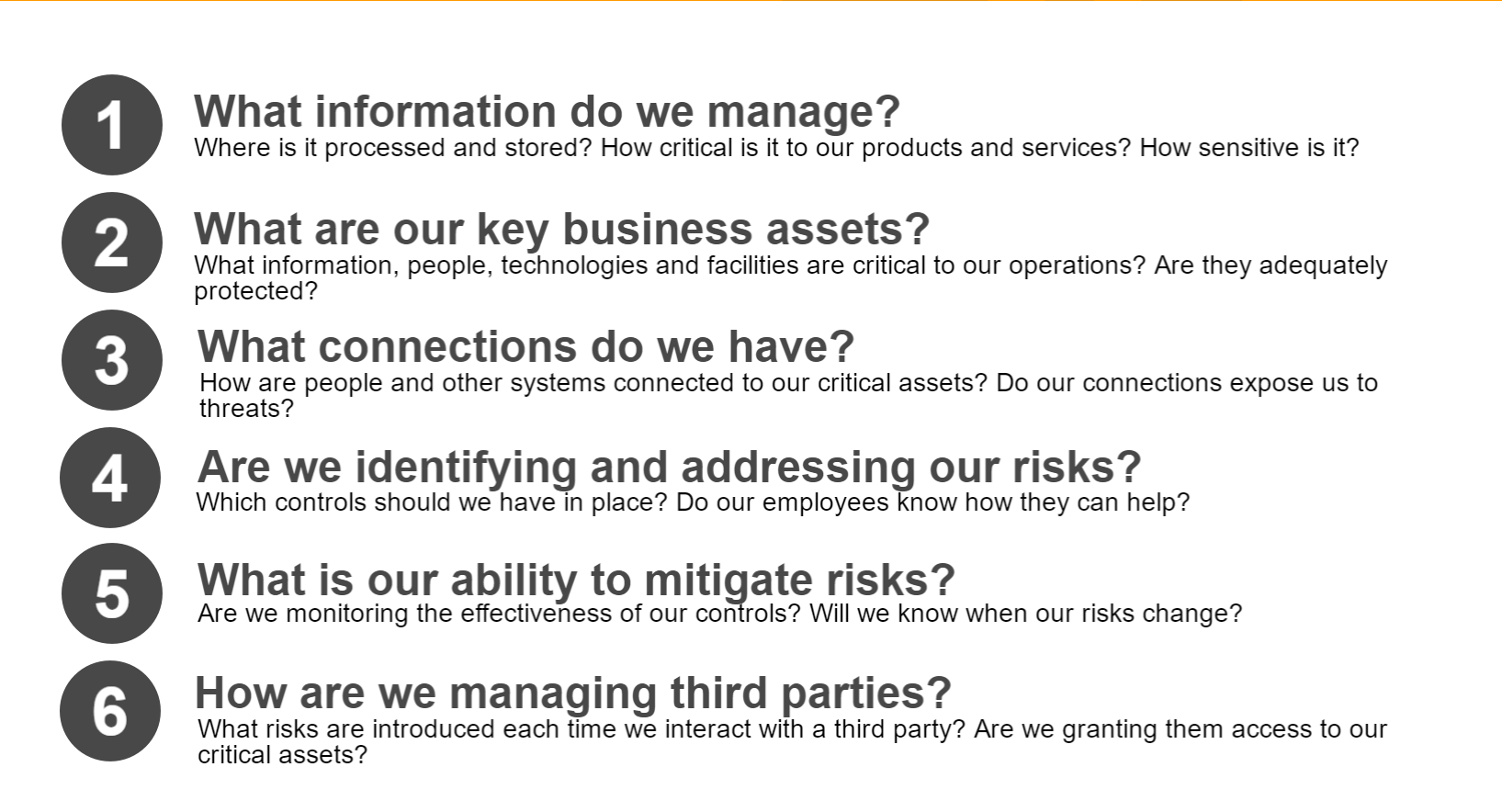
Once you’ve self-assessed, here are some general VOIP security best practices that everyone should follow.
Implement a Strong Password Policy
It might seem obvious, but brute force attacks (where hackers attempt to guess your passwords) are behind a huge percentage of data leaks.
For best results, tell employees to change their passwords at least once every two weeks, ensure they’re not using the same passwords for multiple accounts, and instruct them to avoid using any personal or public information (street address number, pet’s name, etc.) in work passwords.
Avoid Using Public WiFi
Public WiFi is a breeding ground for hacking since malware and other viruses can easily be spread over an unsecured network.
Tell team members never to use unsecured WiFi on work devices.
Conduct Frequent Security Audits
Even a simple lapse in network security has a major impact on the quality and security of VoIP calls. Optimally, security assessments should be performed by independent and verified security agencies so nothing is overlooked and proper preventative action is taken.
Key factors of an independent security assessment include:
- Gateway assessments – VoIP is transferred to PSTN lines by VoIP gateways, and protection mechanisms need to be in place at these endpoints as well as in other endpoints on your network.
- Firewall configuration – Your firewall needs to keep out cyber criminals and allow data packets you sent out to travel unhindered.
- Cyberattack simulations – These are performed to help your organization assess its vulnerabilities and improve intrusion detection.
- Application-based security scanning – An average business network uses multiple applications for a variety of functions, and each should be scanned for issues.
- Patching procedures – Patching procedures should also be assessed to determine if software/hardware has weaknesses that might be exploited
Protect BYOD/Mobile Devices
Mobile VoIP apps are ideal for offices with remote/blended teams, often on properly secured networks.
However, if the mobile device or BYOD device is used over public WiFi for VoIP, they’re highly vulnerable to cybercriminals thanks to unsecure 802.11x wireless connections.
To prevent this, enable end-to-end encryption, and protect wireless access points through more secure protocols than 802.11x. These include WPA, which uses encryption to protect connected devices.
Additionally, a session border controller helps remote employees connect to SIP trunks while analyzing all incoming and outgoing VoIP traffic for vulnerabilities and attacks.
Run Consistent Software and System Updates
Even though many VoIP providers run automatic software updates, it’s still a good idea to ensure that you’re using the latest version of all your business communication tools.
These updates don’t just upgrade features and improve the user experience. They also contain essential security updates and protection against viruses and malware you may not even know exist.
Additionally, they often introduce technology to fix packet loss and shore up weaknesses.
For most VoIP phones, the trivial file transfer protocol (TFTP) is the primary system for delivering security patches. Unfortunately, this presents a security vulnerability because any hacker can present a simple file into the system that exposes vulnerabilities and provides an entry point into the network.
To prevent this, security measures need to be in place for protecting hardware from fraudulent patching, and VoIP phones must be regularly patched by IT staff to prevent any vulnerabilities from being exploited.
The Most Secure & Encrypted VoIP Providers
When it comes to security, and especially encryption, not all VoIP providers are created equal.
Providers offering encryption and superior security features are outlined in the table below.
| Provider | 8×8 | RingCentral | Nextiva | Vonage | GoToConnect |
| Uptime | 99.9999% | 99.999% | 99.999% | 99.999% | 99.999% |
| End-to-End Encryption | ✓ | ✓ | ✓ | ✓ | ✓ |
| Support Hours | Phone: Monday-Saturday, 6:00 AM-6:00 PM
Chat Support: 24/7 |
Phone: 5:00 AM-6:00 PM Monday-Friday
Chat Support: 24/7 |
Phone: 5:00 AM-6:00 PM Monday-Friday
Chat Support: 24/7 |
Phone: 24/7
Chat Support: 24/7 |
|
| HIPAA Compliance | ✓ | ✓ | ✓ | ✓ | ✓ |
| ISO-27001 Certification and SOC 2 Compliance | ✓ | ✓ | ✓ | ✓ | ✓ |
| Independent Security Audits | Annually | Annually | Regular Penetration Testing | Independent Security Audits, Frequency Unknown | Annually |
| More Information | Our 8×8 Review | Our RingCentral Review | Our Nextiva Review | Our Vonage Review | Our GoToConnect Review |
To learn more about the encrypted VoIP providers we’ve mentioned here, and to discover other business communication solutions, check out our interactive table of top business VoIP software.
VoIP Security FAQs
Below, we’ve answered some of the most common VoIP security questions.
A Virtual Private Network (VPN) is a secure network that hides your IP address, location, and more from your Internet Service Provider and the websites you access, allowing you to browse the Internet anonymously.
It works by rerouting your data through the VPN provider’s own private servers, which have strong data encryption policies in place like AES 256-bit encryption, SSL, TLS, and more.
For additional information on VPNs, check out our Guide to VoIP VPN.
One of the best things you can do to prevent a cyber attack is to avoid using public, unsecured WiFi on any device that contains work data.
Additionally, make sure you’re using proper WiFi encryption protocols.
Wired Equivalent Privacy, (WEP) WiFi Protected Access, (WPA), and WiFi Protected Access Version 2 (WPA2) are the top three available, with WPA2 usually being the best choice.
For best results, update your security strategy and privacy policy at least once a year. It’s a smart idea to hire a third-party Security Monitoring and Management professional to help you evaluate your current plan and identify gaps.
The security strategy -- and therefore, budget -- for each business will be based on factors like size, legal compliance requirements, specific industries, the types of data stored, and more.
In general, a good rule of thumb is that a cybersecurity strategy should cost roughly 9%-15% of your annual IT budget.
In addition to turning off features like location tracking and always ensuring you have a passcode/PIN in place, to protect your smartphone:
- Turn Bluetooth connectivity off when it is not in use
- Turn off automatic WiFi connectivity
- Turn off autocomplete features
- Enable two-factor authentication
- Enable “Find my Phone” features