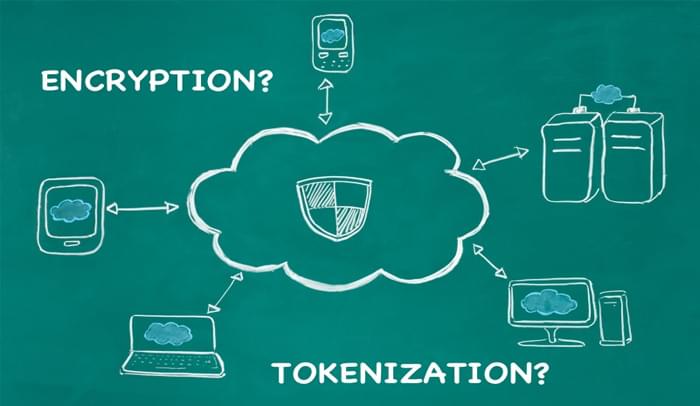
Cloud computing is becoming more and more important to the average company, but with all of that data shuttling back and forth from remote vendor systems, through the cloud, to client networks and back, what about comprehensive security?
Certain kinds of security tools provide security for data at rest, data that is stored on-site. But it’s another thing when sensitive information and things like customer identifiers (social security numbers) are bouncing around in connected networks.
Enter the cloud encryption gateway, a solution for data traffic security. A cloud encryption gateway encrypts sensitive data at a point of entrance and egress, so that it can move around outside of a client network, impervious to all sorts of sneaking and snooping. One way to think about this is as a “packaging tunnel” for data, where as the data flows out, it is neatly wrapped up in protective encryption.
Why Use Cloud Encryption Gateways?
Besides the evident security of having all outgoing data encrypted, there are other reasons professionals point to for having data run through one of these resources.
A big one is the preservation of core functionality, where with the wrong kinds of security, data is as opaque to the legitimate end user as it would be to a hacker. By contract, many kinds of cloud encryption gateways, as this factsheet from Perspecsys puts it, allow companies to “preserve the end user’s experience with the cloud application even while securing the data being processed and stored in the cloud.”
Preserving SaaS or cloud functionality is one of the major value propositions around some of the popular cloud encryption gateway solutions now available. Other benefits include lowering latency across a network, and promoting more open, effective platforms.
Those Troublesome Keys
So a cloud encryption gateway can be great for outbound encryption, but how do companies actually utilize these resources?
One very important aspect of cloud encryption gateway design is the question of who holds and controls the encryption keys.
Early in the month, we spoke to Josh Danielson, a Cloud Security Manager with Axway. Danielson, who has almost a decade of experience in IT security, holds a Master of Science degree in Information Management from Syracuse University, along with multiple certifications including CISSP-ISSAP and CISM.
Danielson said companies face a two-fold challenge: making sure that they, and not service providers hold the keys, and managing not to compromise them.
“Organizations are beginning to realize the importance of encryption when outsourcing to Cloud Service Providers.” Danielson said. “But the devil is in the details. Who has access to encryption keys is a lesson that organizations are just starting ask.”
In addition, Danielson said, businesses without the right internals protocols for keeping tabs on keys can lose valuable data. Danielson said there is “zero margin for error” in maintaining these encryption keys, and that is where many firms go wrong.
Some of today’s best cloud encryption gateway reviews, and reports on technology in the field, reflect the importance of managing encryption keys, as in this guide from April 2013 piece from Network World. In “The state of cloud encryption: from fiction to actionable reality,” writer Debabrata Dash, Ph.D. stresses the need for the primary enterprise stakeholder, the client, to hold the keys.
“If the cloud service provider controls the keys, cloud data is still at risk from hackers, hactivists, insider fraud or disclosures to law enforcement.” Dash writes. “Key retention by the enterprise ensures no third party — whether law enforcement, cloud provider system administrators or cybercriminals — can access sensitive information in the cloud without first contacting the data owner.”
Key Management Solutions
This kind of encryption key management can seem daunting, but, says Danielson, there is a solution: Amazon Web Services has just come out with a service called AWS Key Management Service, or KMS, that is essentially a resource for creating and maintaining the keys that a company uses for encryption. Users can define usage policies for keys, and audit key use. KMS is compatible with a host of other AWS services. And, according to Amazon, the places that keys are kept are “highly durable.”
“AWS KMS stores multiple copies of encrypted versions of your keys in systems that are designed for 99.999999999% durability to help assure you that your keys will be available when you need to access them.” – reads a fact sheet from AWS.
Danielson and others give AWS KMS high marks on price, performance and functionality, and promote this service as a useful ways to manage that key handling problem.
Other Tips for Implementation
Another good principle for cloud encryption gateway setups, says Danielson, is to start early.
“In order to deliver a successful implementation, one of the most effective and coincidentally easiest things to do, is to start early.” Danielson says. “Simple advice, but by doing so this will allow organizations to avoid down time when having to migrate existing storage, to a secured medium. ”
In any type of migration, starting early and having a plan makes a big difference. The business world abounds with stories of “epic fail disruption” where companies tried to take on too much, too soon, without having staff and training resources in place. Then there are other cases of practical “IT piracy” where a hapless client has a vendor holding data or resources ‘hostage,’ because they didn’t look closely enough or negotiate a contract up front. The bottom line is that implementation matters, and it’s especially important in systems like these where taking advantage of a catch-all solution requires holding onto the reins. Much like drivers pat their pockets for their car keys, companies have to continually monitor their IT upgrades to make sure they are being done right.
Having cloud encryption gateway solutions on the market helps companies to benefit from better comprehensive security for the most sensitive data assets they hold. Knowing more about the practical use of the encryption helps leaders to walk that fine line between outsourcing and keeping control in-house, to plan well and avoid the pitfalls of modern cloud security vulnerabilities.